What is a STUN Server? A Complete Guide (2025)
Introduction to STUN Servers
In the world of real-time digital communications, seamless connectivity is crucial. Whether you’re making a VoIP call, joining a video conference, or playing an online game, establishing direct and reliable peer-to-peer connections is essential. This is where STUN servers come into play. But what is a STUN server exactly?
A STUN (Session Traversal Utilities for NAT) server is a network service that helps devices behind routers and firewalls discover their public IP address and port mappings. This knowledge is indispensable in overcoming the challenges posed by NAT (Network Address Translation), which is prevalent in most private networks. STUN servers ensure that real-time communication tools like VoIP, video calls, and WebRTC applications can establish direct connections, even in complex networking scenarios. Understanding the STUN protocol and its practical implementation is vital for developers working on modern communication software in 2025.
Understanding the Basics: STUN Protocol and Network Address Translation (NAT)
What is NAT and Why Does it Matter?
Network Address Translation (NAT) is a technique used by routers to allow multiple devices on a private network to share a single public IP address. While NAT enhances security and conserves IP addresses, it also creates challenges for peer-to-peer communication. Devices operating behind NAT cannot easily determine their public-facing IP and port, making direct connections with external peers difficult.
For developers building cross-platform solutions, understanding NAT traversal is especially important when working with frameworks like
flutter webrtc
, which enables real-time communication on both Android and iOS.How STUN Helps with NAT Traversal
STUN servers address this problem by enabling clients to discover their public IP address and the specific port mappings created by NAT devices. When a client wants to initiate a connection, it sends a request to a STUN server, which responds with the public endpoint. This information is then used to facilitate peer-to-peer connections, even when both parties are behind NATs.
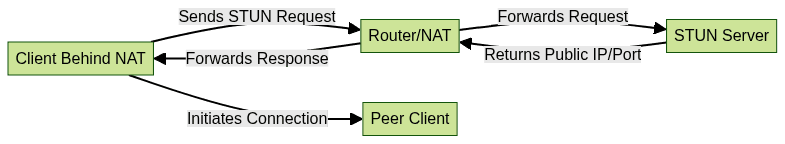
This process enables applications to establish peer-to-peer connectivity with minimal manual configuration, streamlining real-time communication in diverse networking environments. For those developing on Android, leveraging
webrtc android
can simplify the integration of STUN and NAT traversal in your mobile apps.How a STUN Server Works
The Role of UDP and TCP in STUN Communication
The STUN protocol primarily uses UDP (User Datagram Protocol) because it is lightweight and suitable for time-sensitive, real-time communication. UDP allows clients to quickly exchange minimal packets with the server, reducing latency. However, STUN can also operate over TCP for environments where UDP is blocked or unreliable, ensuring greater compatibility across varied network setups.
If you're building real-time features for your web application, you might consider using a
javascript video and audio calling sdk
to streamline development and ensure robust connectivity.STUN Protocol Workflow Step-by-Step
Let’s break down the typical workflow of a STUN server:
- Client Initiates Request: The client sends a STUN binding request to the server, usually over UDP.
- Server Receives Request: The STUN server receives the request and captures the client’s public IP address and port from the packet.
- Server Sends Response: The server replies to the client with a message containing the public IP and port.
- Client Uses Mapping: The client uses this information to communicate with peers or to facilitate NAT traversal in protocols like ICE (Interactive Connectivity Establishment).
Example: Simplified STUN Request/Response in Python (using UDP)
1import socket
2
3STUN_SERVER = ("stun.l.google.com", 19302)
4MESSAGE = b"\x00\x01\x00\x00" # Simplified STUN binding request
5
6sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
7sock.sendto(MESSAGE, STUN_SERVER)
8response, _ = sock.recvfrom(2048)
9print(f"Received response: {response}")
10This snippet demonstrates how a client can send a basic STUN request to a public server and handle the response, which will contain the mapped public IP and port.
Key Use Cases for STUN Servers
STUN in VoIP and Video Conferencing
VoIP (Voice over IP) and video conferencing applications rely on STUN servers to enable direct media streams between participants. By discovering the public endpoints of each client, STUN allows for low-latency, peer-to-peer audio and video transmission, reducing server load and improving call quality. For developers looking to add such capabilities, integrating a
Video Calling API
can accelerate the process and ensure high-quality, scalable communication.STUN in WebRTC Applications
WebRTC (Web Real-Time Communication) leverages STUN servers extensively for browser-based voice, video, and data sharing. When two browsers attempt to connect, they use STUN to learn their public addresses and initiate direct connections, even across different networks and NAT types. This makes STUN a foundational technology for real-time web apps in 2025. If you want to quickly add video calling features to your app, you can
embed video calling sdk
for a seamless integration experience.STUN vs TURN vs ICE: What’s the Difference?
While STUN is effective for most NAT traversal scenarios, it has limitations. Some networks use symmetric NATs or restrictive firewalls that block direct peer connections, even with STUN’s help. This is where TURN and ICE protocols come into play.
When is a TURN Server Needed?
A TURN (Traversal Using Relays around NAT) server acts as a relay for media streams when direct peer-to-peer connections are impossible. Unlike STUN, which only discovers public addresses, TURN relays the actual data between clients, ensuring connectivity at the expense of increased latency and bandwidth usage. TURN servers are essential in highly restrictive networking environments. For applications that require reliable voice communication, exploring a
phone call api
can help you find the best solution for your needs.ICE: Integrating STUN and TURN for Seamless Connectivity
ICE (Interactive Connectivity Establishment) is a framework that combines STUN and TURN to optimize peer-to-peer connectivity. ICE first tries to use STUN for direct communication; if that fails, it falls back to TURN relays.
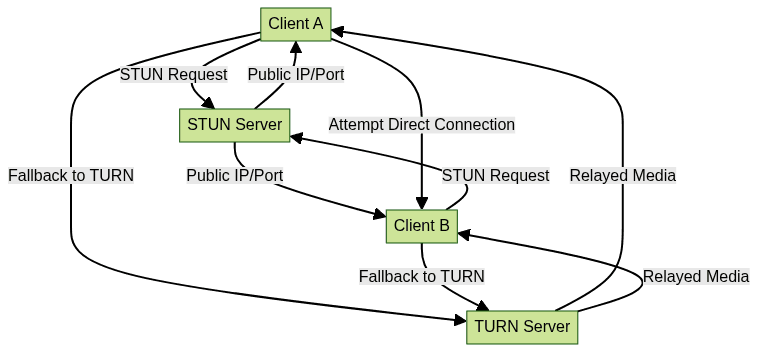
The ICE process ensures that connections are established using the most efficient and direct route possible, only using TURN if absolutely necessary. For those building cross-platform mobile apps, using a
react native video and audio calling sdk
can help you implement ICE, STUN, and TURN with minimal effort.Implementing a STUN Server: Practical Steps
Popular Open Source STUN Servers
Developers have access to several robust open source STUN server implementations. Some of the most popular in 2025 include:
coturn
: A widely-used STUN/TURN server with comprehensive features.stund
: A lightweight STUN server suitable for learning and experimentation.reTurnServer
: Part of the reSIProcate SIP stack, supporting STUN and TURN.
If you're developing with Flutter, check out
flutter webrtc
for guidance on integrating STUN and TURN in your cross-platform apps.Sample STUN Server Configuration
Below is a basic example of a coturn configuration file (
turnserver.conf):1listening-port=3478
2fingerprint
3lt-cred-mech
4realm=example.org
5user=testuser:testpassword
6This configuration sets up a STUN/TURN server listening on port 3478 with a test user. For production deployments, always secure credentials and consider additional hardening.
Common Implementation Challenges and How to Overcome Them
Implementing a STUN server can be challenging due to NAT variations, firewall restrictions, and port mapping inconsistencies. Developers should:
- Conduct thorough NAT type detection
- Use ICE to handle network edge cases
- Regularly test with different NAT/firewall setups
- Monitor server logs for failed connections
Proper diagnostic tools and robust fallbacks (like TURN) are critical for reliability. For a ready-to-use solution, consider integrating a
Video Calling API
to handle these complexities for you.Security Considerations for STUN Servers
STUN servers, while not directly handling media streams, can expose your network to certain risks. Attackers might misuse open STUN servers for reflection attacks or enumeration. To mitigate risks:
- Restrict access to trusted networks where possible
- Enable authentication and credentials (especially for TURN)
- Monitor for abnormal request patterns
- Keep server software updated with the latest security patches
Applying these best practices ensures your STUN infrastructure remains secure, efficient, and reliable in 2025.
Troubleshooting and Best Practices
Common issues with STUN servers include:
- Failure to obtain public IP/port (often due to restrictive firewalls or symmetric NAT)
- High packet loss or latency (network congestion)
- Misconfiguration of server or client settings
Best practices:
- Always test with multiple STUN servers for redundancy
- Enable verbose logging for easier diagnostics
- Regularly update software and review network policies
- Integrate ICE to automate fallback and connectivity checks
A reliable STUN setup is the foundation of robust real-time communication systems. If you want to experience these features firsthand,
Try it for free
and explore how modern APIs can simplify your development process.Conclusion: Why Understanding STUN Servers Matters
In today’s interconnected world, real-time communication is the backbone of countless applications. Mastering STUN servers and their role in NAT traversal enables developers to build performant, reliable, and scalable voice, video, and peer-to-peer solutions. As networking environments grow more complex in 2025, a solid grasp of STUN, TURN, and ICE is essential for any modern software engineer or IT architect.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ