STUN Server: A Comprehensive Guide for Developers
STUN (Session Traversal Utilities for NAT) servers are essential components for enabling real-time communication applications that need to traverse Network Address Translation (NAT). This guide provides a comprehensive overview of STUN servers, covering everything from the underlying STUN protocol to implementation, configuration, and troubleshooting. Whether you're developing a WebRTC application, VoIP service, or online game, understanding STUN servers is crucial.
What is a STUN Server?
A STUN server is a network server that helps devices behind NATs discover their public IP address and the type of NAT they are behind. This information is critical for establishing direct peer-to-peer (P2P) connections, which are vital for real-time communication applications. Without a STUN server, devices behind NATs would struggle to communicate directly, leading to connectivity issues and a degraded user experience.
STUN servers implement the STUN protocol, which allows a device to send a request to the server. The server then responds with the device's public IP address and port, as seen from the outside world. This process enables the device to learn how other devices on the internet can reach it, even if it's behind a NAT.
What are STUN Servers Used For?
STUN servers are primarily used to facilitate NAT traversal in applications that require direct peer-to-peer communication. Key use cases include: WebRTC applications for video and audio conferencing, VoIP services for making internet-based phone calls, and online gaming for enabling multiplayer interactions. By allowing devices behind NATs to discover their external IP address and port, STUN servers enable these applications to establish direct connections, improving performance and reducing latency.
How STUN Servers Work
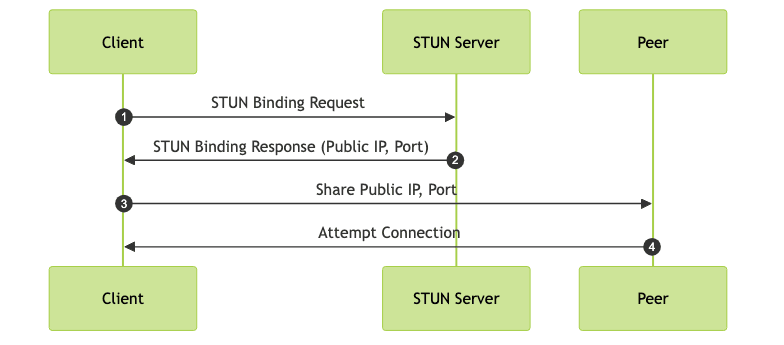
The process begins with a client (e.g., a WebRTC application running in a browser) sending a STUN binding request to the STUN server. The STUN server, residing on a public network, examines the source IP address and port of the incoming request. It then formulates a STUN binding response, containing the discovered public IP address and port, and sends it back to the client. The client can then use this information to share with other peers, allowing them to attempt direct connections. The whole process can be described using the following diagram.
Understanding the STUN Protocol
The STUN protocol is the foundation upon which STUN servers operate. It's a lightweight protocol designed for discovering a device's public IP address and port when it's behind a NAT. The protocol is based on a request-response model, where a client sends a request to a STUN server, and the server responds with the client's mapped address (public IP and port).
STUN is primarily used with UDP, but it can also be used with TCP. It's an essential component of ICE (Interactive Connectivity Establishment), a framework used by WebRTC to establish connections between peers. ICE uses STUN to discover candidates (possible connection addresses) and then tries to connect using these candidates. If direct connections aren't possible, ICE can fall back to using a TURN server to relay traffic.
The STUN protocol is designed to be simple and efficient, minimizing overhead and maximizing performance. This is crucial for real-time communication applications where low latency is essential. The protocol defines several message types and attributes that are used to exchange information between the client and the server.
RFCs and Standards
The STUN protocol is defined in several RFCs (Request for Comments), which are documents that specify the standards and protocols used on the internet. The most important RFC for STUN is RFC 5389, which obsoletes older RFCs such as RFC 3489. These RFCs define the message formats, attributes, and procedures for the STUN protocol, ensuring interoperability between different STUN server implementations. Adhering to these standards is crucial for building robust and reliable STUN servers.
Key STUN Message Types
The STUN protocol defines several message types, with the most common being the Binding Request and Binding Response. The Binding Request is sent by the client to the STUN server to request its mapped address. The Binding Response contains the client's public IP address and port, as seen by the STUN server. Other message types include Shared Secret Request and Shared Secret Response, which are used for authentication purposes. Error responses are also defined to indicate any problems that occurred during the request processing.
STUN Attributes
STUN messages consist of a header followed by a set of attributes. Attributes are key-value pairs that contain additional information about the message. Common STUN attributes include:
MAPPED-ADDRESS (the client's mapped address), RESPONSE-ADDRESS (the address to which the response should be sent), CHANGE-REQUEST (used to request a change in the IP address or port used by the server), and ERROR-CODE (used to indicate an error condition). These attributes allow clients and servers to exchange detailed information about the connection and any potential issues.STUN vs. TURN: Key Differences
While both STUN and TURN servers are used for NAT traversal, they serve different purposes and operate in fundamentally different ways. STUN servers help clients discover their public IP address and port, allowing them to attempt direct connections. However, STUN only works if the NAT allows direct connections between peers after the initial mapping is established. In cases where the NAT is more restrictive (e.g., symmetric NAT), STUN alone is insufficient.
This is where TURN (Traversal Using Relays around NAT) comes in. A TURN server acts as a relay, forwarding traffic between peers when direct connections are not possible. The client establishes a connection to the TURN server, and the TURN server forwards traffic to the other peer. This allows communication to occur even when both peers are behind restrictive NATs. Therefore, STUN assists peers in discovering how to connect, while TURN provides a relay if direct connection fails. TURN servers require more resources than STUN servers, because they are actively relaying traffic.
TURN Server Functionality
TURN servers function as intermediaries, relaying data between peers that cannot establish a direct connection due to NAT restrictions. A client first authenticates with the TURN server. Upon successful authentication, the client requests the TURN server to allocate a relay address. The client then communicates with its peer via this relay address, with the TURN server forwarding traffic in both directions. This ensures connectivity even when direct peer-to-peer communication is impossible.
Choosing Between STUN and TURN
The choice between STUN and TURN depends on the specific network conditions and NAT types involved. In many cases, a STUN server is sufficient for enabling direct connections. However, when dealing with restrictive NATs, a TURN server is necessary. A common approach is to use both STUN and TURN servers in combination. ICE (Interactive Connectivity Establishment) uses STUN to try direct connections first, and then falls back to TURN if direct connections fail. This provides the best of both worlds, minimizing latency when direct connections are possible and ensuring connectivity in all cases.
Implementing a STUN Server
Implementing a STUN server involves several steps, including choosing a programming language, selecting an open-source library, setting up the server, and testing its functionality. There are several open-source STUN server implementations available, making the process relatively straightforward. Here's a detailed guide to implementing your own STUN server:
Choosing a Programming Language
You can implement a STUN server in various programming languages, including C, C++, Go, and Python. The choice depends on your familiarity with the language, performance requirements, and the availability of suitable libraries. C and C++ offer the best performance, while Go and Python are easier to develop and maintain.
Open-Source STUN Server Libraries
Several open-source STUN server libraries are available, simplifying the implementation process. Coturn is a popular and widely used open-source TURN and STUN server. It's robust, well-documented, and supports various features, including TLS encryption and authentication. libjingle (now part of WebRTC) also includes STUN client and server implementations. Other options include custom implementations in languages like Go or Python, leveraging network programming libraries.
Setting up a STUN Server (Example using Coturn) (Approx. 200 words)
Coturn is a great option for setting up a STUN server. Here's a basic example of how to install and configure Coturn:
- Install Coturn:
bash sudo apt-get update sudo apt-get install coturn - Configure Coturn:
Modify the
/etc/turnserver.conffile. Here's a minimal configuration example:
1listening-port=3478
2listening-ip=0.0.0.0
3relay-ip=0.0.0.0
4external-ip=<YOUR_PUBLIC_IP>
5lt-cred-mech
6realm=yourdomain.com
7user=test:test
8Replace
<YOUR_PUBLIC_IP> with the public IP address of your server. You can also set up users for authentication. The lt-cred-mech option enables long-term credential mechanism.- Start Coturn:
bash sudo systemctl start coturn sudo systemctl enable coturnThis will start the Coturn service and configure it to start automatically on boot.
1#!/bin/bash
2# Basic Coturn setup script
3
4# Update package list
5sudo apt-get update
6
7# Install Coturn
8sudo apt-get install coturn -y
9
10# Configure Coturn (replace with your actual settings)
11sed -i 's/^#listening-port=3478/listening-port=3478/' /etc/turnserver.conf
12sed -i 's/^#listening-ip=127.0.0.1/listening-ip=0.0.0.0/' /etc/turnserver.conf
13sed -i 's/^#relay-ip=127.0.0.1/relay-ip=0.0.0.0/' /etc/turnserver.conf
14sed -i 's/^#external-ip=/external-ip=<YOUR_PUBLIC_IP>/' /etc/turnserver.conf
15sed -i 's/^#lt-cred-mech/lt-cred-mech/' /etc/turnserver.conf
16sed -i 's/^#realm=example.com/realm=yourdomain.com/' /etc/turnserver.conf
17sed -i 's/^#userdb=/etc/turnuserdb.conf/user=test:test/' /etc/turnserver.conf
18
19# Start and enable Coturn
20sudo systemctl start coturn
21sudo systemctl enable coturn
22
23echo "Coturn server setup complete. Remember to replace <YOUR_PUBLIC_IP> and configure users."
24Testing Your STUN Server (Approx. 50 words)
After setting up your STUN server, it's crucial to test its functionality. You can use online STUN server testing tools or WebRTC debugging tools to verify that your server is correctly reporting your public IP address and port. Successful testing confirms that your server is properly configured and ready to be used by your applications.
Advanced STUN Server Configuration and Optimization
Once you have a basic STUN server setup, you can further optimize it for security, performance, and scalability. Advanced configuration involves implementing security measures, tuning performance parameters, and ensuring high availability.
Security Considerations
Security is paramount when running a STUN server. Implement strong authentication mechanisms to prevent unauthorized access. Use TLS encryption to protect the communication between clients and the server. Regularly update your STUN server software to patch any security vulnerabilities. Consider implementing rate limiting to prevent denial-of-service attacks. Ensure that your server is properly firewalled to prevent unauthorized access from the outside world.
Performance Tuning
To optimize STUN server performance, tune parameters such as the number of worker threads, the size of the UDP buffer, and the timeout values. Monitor server resource usage (CPU, memory, network) and adjust parameters accordingly. Use a high-performance network interface card (NIC) to maximize network throughput. Consider using a load balancer to distribute traffic across multiple STUN servers.
Scalability and High Availability
For high-traffic applications, ensure that your STUN server can scale to handle the load. Use a cluster of STUN servers behind a load balancer to distribute traffic and provide redundancy. Implement a failover mechanism to automatically switch to a backup server in case of a failure. Use a distributed database to store configuration data and user credentials, ensuring consistency across all servers.
Monitoring and Logging
Implement comprehensive monitoring and logging to track server performance and identify potential issues. Monitor key metrics such as CPU usage, memory usage, network throughput, and the number of active connections. Log all significant events, including connection attempts, errors, and security events. Use a centralized logging system to collect and analyze logs from multiple servers.
Common STUN Server Use Cases
STUN servers are widely used in various applications that require real-time communication and NAT traversal.
WebRTC Applications
WebRTC (Web Real-Time Communication) relies heavily on STUN servers to establish peer-to-peer connections between web browsers. STUN servers enable WebRTC applications to discover the public IP address and port of the browser, allowing direct communication even when the browser is behind a NAT. This is crucial for video conferencing, screen sharing, and file transfer applications.
VoIP and Video Conferencing
VoIP (Voice over Internet Protocol) and video conferencing systems use STUN servers to enable users behind NATs to make and receive calls. STUN servers allow these systems to establish direct connections between users, improving audio and video quality and reducing latency. Without STUN servers, VoIP and video conferencing would be significantly more difficult to implement.
Online Gaming
Online gaming applications use STUN servers to enable multiplayer interactions. STUN servers allow players behind NATs to connect to each other, enabling real-time gameplay. This is particularly important for games that require low latency and high bandwidth, such as first-person shooters and real-time strategy games. STUN combined with TURN ensures players can connect regardless of their NAT configuration.
Troubleshooting Common STUN Server Issues
Even with proper configuration, STUN servers can sometimes encounter issues. Here are some common problems and how to troubleshoot them:
Firewall Issues
Firewalls can block STUN traffic, preventing clients from discovering their public IP address and port. Ensure that your firewall allows UDP traffic on port 3478 (the default STUN port). If you're using TLS, allow TCP traffic on port 3479.
Port Conflicts
If another application is using the same port as your STUN server, it can cause conflicts. Ensure that no other application is using port 3478 or 3479. You can use the
netstat command to check for port conflicts.Connectivity Problems
Connectivity problems can be caused by various factors, including network outages, incorrect STUN server configuration, or client-side issues. Verify that your STUN server is reachable from the internet. Check your STUN server configuration for errors. Use a STUN client to test connectivity from different network locations. Review the logs for potential error messages related to failing connectivity attempts.
Further Resources:
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ