Introduction to the STUN Protocol
Network address translation (NAT) is ubiquitous in modern networking, but it creates challenges for real-time, peer-to-peer communication. The STUN protocol—Session Traversal Utilities for NAT—addresses these obstacles by enabling devices behind NATs to discover their public IP addresses and the type of NAT in use. This capability is essential for applications like VoIP, video conferencing, and other real-time communication platforms.
STUN is a lightweight, stateless protocol that operates over UDP and helps endpoints establish direct connections even when separated by NAT devices or firewalls. In today's networking landscape, where seamless connectivity and low-latency communication are vital, understanding STUN's role, operation, and configuration is crucial for developers and network engineers.
This guide will explore how the STUN protocol works, its components, real-world applications, differences from related protocols like TURN and ICE, protocol details, Cisco device configurations, and best practices for reliable NAT traversal.
How the STUN Protocol Works
Session Traversal Utilities for NAT (STUN) is designed to help devices determine their public-facing IP address and the port mapped by NAT devices. Its primary role is to facilitate NAT traversal, which is critical for enabling real-time communication over the Internet when endpoints are behind routers or firewalls performing network address translation.
NAT Traversal for Real-Time Communication
When a device (STUN client) wants to establish a connection with a peer, it sends a request to a publicly reachable STUN server. The STUN server then responds with the client’s public IP address and port as seen by the outside world. This information enables the client to communicate directly with other endpoints, bypassing the limitations imposed by NAT.
Step-by-Step Workflow
The following mermaid diagram illustrates a typical STUN exchange:
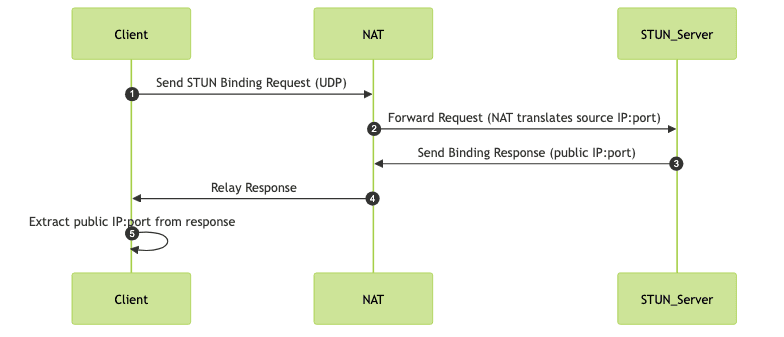
This workflow allows the client to learn how its traffic is mapped by the NAT, which is vital for establishing peer-to-peer connections in applications like WebRTC.
Key Components of the STUN Protocol
STUN architecture involves two main entities: the STUN client and the STUN server.
- STUN Client: Typically, an endpoint or application seeking to discover its public IP and port.
- STUN Server: A publicly accessible server that receives and responds to STUN requests, revealing the external mapping for the client.
Binding Requests and Responses
The fundamental operation in STUN is the binding request-response transaction. The client sends a binding request to the server, which then replies with a binding response containing the observed external address and port.
Example STUN Binding Request (Pseudo-Code)
1STUN_Message = {
2 "type": "BindingRequest",
3 "transaction_id": generateRandomId(),
4 "attributes": []
5}
6sendUdpPacket(STUN_Server_IP, STUN_Server_Port, STUN_Message)
7The server's response informs the client of its public address, enabling further NAT traversal logic.
STUN in Real-World Applications
STUN is integral to a variety of real-time communication scenarios, particularly in VoIP and video conferencing solutions.
STUN in VoIP and Video Conferencing
Protocols like SIP rely on STUN to help endpoints discover their public addresses and negotiate media paths, even when behind NAT devices. For video conferencing, STUN ensures minimal latency by allowing direct media transmission between clients.
Usage in WebRTC and ICE
WebRTC, a standard for browser-based real-time communication, uses Interactive Connectivity Establishment (ICE), which heavily relies on STUN for gathering candidate IP addresses. ICE orchestrates the process of determining the most efficient route for peer-to-peer connections, using STUN for public IP discovery and TURN for relay services when direct connectivity fails.
Interaction with TURN Servers
When direct connectivity via STUN is not possible (e.g., due to symmetric NAT or strict firewalls), communication is relayed through a TURN server. This ensures connection reliability at the cost of higher latency.
Example Scenario (Mermaid Sequence Diagram)
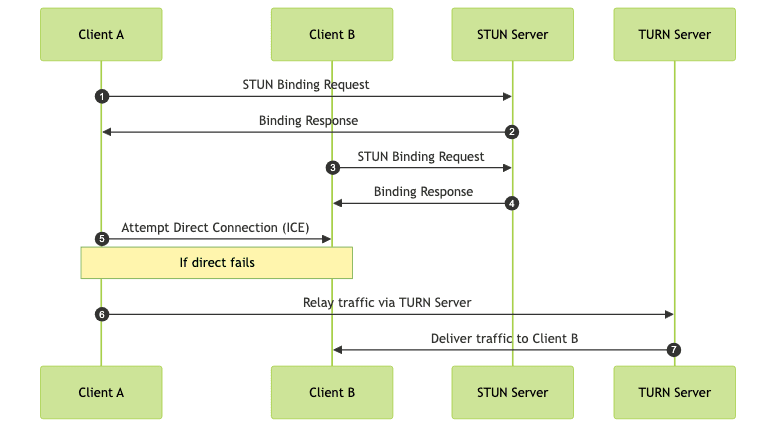
STUN vs. TURN and Other NAT Traversal Techniques
While STUN is fundamental for NAT traversal, it’s often used together with other protocols:
- STUN: Discovers public IP and port; enables direct peer-to-peer connections when possible.
- TURN: Relays traffic when direct connections fail. Used as a fallback.
- ICE: Orchestrates the use of STUN and TURN to establish the most efficient connection.
When to use each? Use STUN when NAT is permissive; rely on TURN when NAT/firewall traversal is otherwise impossible; use ICE for comprehensive peer connection management, as in WebRTC.
Detailed STUN Protocol Operation
STUN messages and attributes are defined in RFC 3489 (original) and RFC 5389 (updated). The protocol operates over UDP or TCP, but UDP is most common due to its low overhead and suitability for real-time communication.
Message Types and Attributes
Common STUN message types:
- Binding Request
- Binding Response
- Binding Error Response
- Shared Secret Request/Response
Attributes include:
- MAPPED-ADDRESS
- XOR-MAPPED-ADDRESS
- USERNAME
- MESSAGE-INTEGRITY
- FINGERPRINT
Security Considerations
While STUN is stateless and lightweight, it’s subject to certain attacks and evasion techniques. Deep Packet Inspection (DPI) and Application Layer Gateways (ALGs) in firewalls may affect STUN traffic. Always consider network security policies and implement authentication (short-term or long-term credentials as per RFC 5389) for sensitive deployments.
STUN Message Structure (Pseudo-Code/JSON)
1{
2 "type": "BindingRequest",
3 "transaction_id": "0x1234567890abcdef",
4 "attributes": {
5 "USERNAME": "user1",
6 "MESSAGE-INTEGRITY": "sha1-hash",
7 "FINGERPRINT": "crc32-hash"
8 }
9}
10Configuring STUN on Cisco Devices
While STUN most commonly refers to NAT traversal, Cisco devices also support Serial Tunnel (STUN) for encapsulating serial data (e.g., SDLC traffic) over IP networks.
Overview of Serial Tunnel (STUN) and SDLC
Cisco STUN enables legacy serial protocols to traverse modern IP networks, supporting migration strategies for older equipment. SDLC (Synchronous Data Link Control) is often tunneled using Cisco’s STUN feature.
Basic vs. SDLC STUN Configuration
Basic STUN configuration involves defining interfaces and peers for encapsulation. SDLC STUN adds protocol-specific parameters.
Sample Cisco STUN Configuration Commands
1interface serial0
2 ip address 10.0.0.1 255.255.255.0
3 encapsulation stun
4 stun peer-address 10.0.0.2
5 stun protocol-group 0 sdllc
6This configuration sets up a serial interface to encapsulate SDLC traffic over IP, using the STUN protocol group.
Best Practices and Common Pitfalls
Recommendations for Deploying STUN
- Deploy geographically distributed STUN servers for reliability and low latency
- Combine STUN with TURN and ICE for comprehensive NAT traversal
- Monitor and log STUN transactions for troubleshooting and analytics
Common Issues and Troubleshooting Tips
- Symmetric NATs may prevent STUN from working; fallback to TURN is required
- Application Layer Gateways (ALGs) on routers/firewalls can interfere with STUN messages
- Deep Packet Inspection may block or throttle UDP traffic
- Ensure proper firewall and router configuration to allow outbound UDP on the required ports
Conclusion
The STUN protocol remains a cornerstone of modern NAT traversal, enabling peer-to-peer and real-time communication in a world filled with NATs and firewalls. Its integration with protocols like ICE and TURN makes it indispensable for VoIP, WebRTC, and beyond. As network topologies evolve, STUN and its related protocols will continue to adapt, ensuring secure and seamless connectivity for next-generation applications.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ