Introduction to Google STUN Server
In our increasingly connected world, seamless peer-to-peer (P2P) communication is vital for modern web applications, especially those relying on real-time media like video conferencing and VoIP. However, most devices sit behind Network Address Translation (NAT) or firewalls, complicating direct connections. This is where the STUN protocol shines, providing a lightweight way to discover public-facing IP addresses and ports.
Among the many public STUN solutions, Google STUN servers are the de facto choice for developers and network engineers building WebRTC, VoIP, and other P2P systems. Google's free and reliable servers empower millions of applications to connect users worldwide.
This guide explores everything developers need to know about Google STUN servers in 2025: how they work, configuration, implementation strategies, troubleshooting, security, best practices, and alternatives. By the end, you’ll be equipped to build robust, real-time communication solutions using Google STUN servers.
What is a STUN Server?
Session Traversal Utilities for NAT (STUN) is a standardized protocol (RFC 5389) that allows devices behind NATs or firewalls to discover their public IP address and port as seen by external servers. This process is foundational for establishing direct peer-to-peer communications, bypassing the complexities of NAT and firewall traversal.
STUN operates by having a client send a request to a publicly accessible STUN server. The server replies with the source IP address and port it sees, informing the client of its external network presence. This knowledge enables applications to share connection details with peers, facilitating direct P2P connectivity.
Common STUN Server Use Cases
- WebRTC: Enables browsers and apps to establish video/audio calls and data channels. For instance, if you're developing for
webrtc android
orflutter webrtc
, integrating STUN is essential for reliable connectivity. - VoIP: Allows SIP endpoints to register and communicate directly across NATs.
- Online Gaming: Supports low-latency, peer-to-peer multiplayer connections.
High-Level STUN Communication Flow
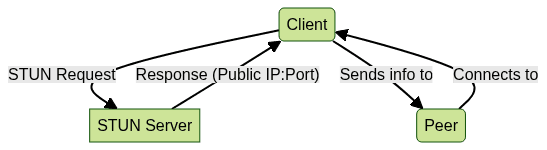
Deep Dive: Google Public STUN Servers
Google maintains several public STUN servers, making them a popular choice for developers due to their reliability and global reach. These servers are ideal for NAT traversal in WebRTC, VoIP, and other P2P applications, and are commonly used alongside solutions like
javascript video and audio calling sdk
for seamless real-time communication.Google STUN Server Addresses and Ports
stun.l.google.com:19302stun1.l.google.com:19302stun2.l.google.com:19302stun3.l.google.com:19302stun4.l.google.com:19302
All Google STUN servers operate on UDP port 19302. They are designed for high availability, distributed geographically, and maintained by Google for public use.
Features and Reliability
- Global Infrastructure: Geographically distributed for low latency and high uptime.
- No Registration Needed: Open access for developers and applications.
- Widely Supported: Default in most WebRTC libraries and frameworks, including those for
python video and audio calling sdk
integration. - Rate Limits: Intended for moderate use, with anti-abuse measures in place.
Comparing Google STUN Servers to Other Public Options
Google’s STUN servers are known for their minimal downtime and consistent performance, outperforming many community-run or less-established public STUN servers. However, for high-volume applications, dedicated or self-hosted STUN servers may be preferable, especially if you're building a custom
Video Calling API
solution.Google STUN Server Addresses (Code Snippet)
A typical WebRTC ICE server configuration using Google STUN servers in JavaScript:
1const iceServers = [
2 { urls: "stun:stun.l.google.com:19302" },
3 { urls: "stun:stun1.l.google.com:19302" },
4 { urls: "stun:stun2.l.google.com:19302" },
5 { urls: "stun:stun3.l.google.com:19302" },
6 { urls: "stun:stun4.l.google.com:19302" }
7];
8
9const rtcConfig = { iceServers };
10How Google STUN Servers Work
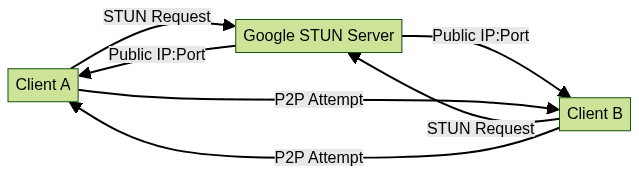
A Google STUN server acts as a simple echo service for NAT traversal. Here’s how the process unfolds:
- Client Initiation: The client (browser or app) sends a STUN Binding Request to a Google STUN server using UDP (sometimes TCP).
- Server Response: The server replies with the observed public IP and port, which the client uses to inform peers.
- Peer Communication: The peer uses this information to attempt direct connectivity.
Step-by-Step STUN-Based NAT Traversal
- Discovery: Client sends a STUN request to
stun.l.google.com:19302. - Response: Server responds with external IP and port.
- Signaling: Client shares its public address with the peer via a signaling service.
- Connection Attempt: Peers try to connect directly using the discovered addresses.
- Fallback: If direct connection fails (e.g., symmetric NAT), a TURN server may be required.
UDP vs. TCP with STUN
- UDP: Preferred for low-latency media streams; most NATs support UDP traversal.
- TCP: Used as fallback when UDP is blocked, but with higher latency.
Security and Privacy Considerations
- STUN only reveals public-facing IP addresses, not private network details.
- Rate limiting and anti-abuse measures help protect Google STUN infrastructure.
- No authentication—do not use for sensitive operations.
Implementing Google STUN Server in WebRTC/VoIP
Integrating Google STUN servers into your application is straightforward, especially with popular libraries and frameworks. Here’s how to configure and use them for WebRTC and VoIP scenarios. If you're working with cross-platform solutions, consider the
react native video and audio calling sdk
for seamless integration on mobile devices.WebRTC Configuration (JavaScript Example)
1const rtcConfig = {
2 iceServers: [
3 { urls: "stun:stun.l.google.com:19302" },
4 { urls: "stun:stun1.l.google.com:19302" }
5 ]
6};
7
8const peerConnection = new RTCPeerConnection(rtcConfig);
9VoIP Configuration (C# Example with SIP.js)
1var configuration = new WebRtcPeerConnectionConfiguration
2{
3 IceServers = new List<IceServer>
4 {
5 new IceServer { Urls = new List<string> { "stun:stun.l.google.com:19302" } },
6 new IceServer { Urls = new List<string> { "stun:stun2.l.google.com:19302" } }
7 }
8};
9Python Example (aiortc)
1from aiortc import RTCIceServer, RTCConfiguration
2
3ice_servers = [
4 RTCIceServer(urls=["stun:stun.l.google.com:19302"]),
5 RTCIceServer(urls=["stun:stun1.l.google.com:19302"])
6]
7
8rtc_config = RTCConfiguration(iceServers=ice_servers)
9Best Practices for Reliability and Fallback
- Multiple STUN Servers: Specify several Google STUN addresses for redundancy.
- Fallback to TURN: Always include TURN in ICE servers for robust NAT traversal.
- Monitor Connectivity: Detect and handle connection failures dynamically.
- Respect Rate Limits: Don’t spam STUN requests; cache results when possible.
- For applications that require embedding communication features, using an
embed video calling sdk
can accelerate development and ensure compatibility with STUN/TURN configurations.
Testing and Troubleshooting Google STUN Server
Ensuring your Google STUN server setup is working correctly is crucial for reliable communication.
Verifying Google STUN Server Functionality
- Check Connectivity: Use developer console logs or network tools to verify STUN requests and responses.
- Online Testers: Tools like Trickle ICE, WebRTC Troubleshooter, and open-source STUN client libraries can help. If you're building telephony features, you might also consider evaluating a
phone call api
for additional capabilities.
Common Issues and Solutions
- Timeouts: Ensure UDP port 19302 is open and not blocked by firewalls.
- Blocked Ports: Switch to a different Google STUN address or try TCP fallback.
- Rate Limiting: Reduce request frequency or rotate between multiple STUN servers.
Python Code Example: Testing Google STUN Server
1import stun
2
3nat_type, external_ip, external_port = stun.get_ip_info(
4 stun_host="stun.l.google.com",
5 stun_port=19302
6)
7print(f"NAT Type: {nat_type}\nExternal IP: {external_ip}\nExternal Port: {external_port}")
8Alternatives and When to Use TURN Servers
While STUN works for most NAT traversal scenarios, it cannot always punch through strict NATs or firewalls. That’s where TURN (Traversal Using Relays around NAT) comes in, acting as a media relay server when direct P2P is impossible. If you're seeking a
jitsi alternative
, exploring different STUN/TURN providers and SDKs can help you find the right fit for your architecture.Key Differences: STUN vs. TURN
- STUN: Discovers public address, enables direct P2P; lightweight; no media relay.
- TURN: Relays traffic through the server; higher latency/cost; works with all NATs/firewalls.
Combining STUN and TURN
Best practice is to include both STUN and TURN servers in your ICE configuration for maximum reliability.
Note: As of 2025, Google does not offer public TURN servers. For TURN, consider open-source solutions like coturn or hosted commercial providers.
Security, Limitations, and Best Practices
Security Considerations
- No Authentication: Anyone can use Google STUN servers; do not transmit sensitive data.
- Rate Limits: Google enforces anti-abuse measures; excessive requests may be throttled.
- Logging: Minimal logging, but always assume public infrastructure may be monitored.
Known Limitations
- No Media Relay: Pure STUN; cannot relay media (use TURN if needed).
- Rate Limiting: Intended for moderate, not massive, traffic.
- No SLAs: No uptime guarantees for mission-critical production use.
Recommendations for Production
- Use Google STUN servers for development, prototyping, and moderate-use apps.
- For large-scale or mission-critical applications, deploy your own STUN/TURN infrastructure.
- Always pair STUN with TURN in ICE lists for maximum NAT traversal success.
Conclusion
Google STUN servers remain a reliable, developer-friendly choice for NAT traversal in WebRTC, VoIP, and peer-to-peer applications in 2025. By understanding their operation, configuration, limitations, and best practices, you can build resilient, real-time communication solutions. For production environments, always combine STUN with TURN and consider self-hosting for complete control.
Ready to start building?
Try it for free
and experience seamless real-time communication integration in your applications.Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ