SIP Network Elements: Architecture, Roles, and Best Practices
Introduction to SIP Network Elements
Session Initiation Protocol (SIP) network elements form the backbone of modern VoIP (Voice over IP) infrastructures. At their core, SIP network elements are hardware or software components that manage signaling, routing, registration, security, and media processing within an IP-based communication environment. The SIP protocol, defined by the IETF, is a flexible, text-based signaling protocol used for establishing, managing, and terminating multimedia sessions—such as voice and video calls—over IP networks.
As enterprises and carriers migrate to IP-based communications, SIP network elements are central to delivering scalable, secure, and interoperable telephony solutions. They ensure calls are routed efficiently, users are authenticated, media streams traverse NATs and firewalls, and that the network remains resilient and secure. In 2025, robust SIP network design is essential for high-quality, carrier-grade VoIP deployments and seamless SIP trunking services.
Overview of SIP Network Elements
SIP network elements each play a distinct role within the overall architecture. Understanding their functions is key to designing resilient and scalable SIP infrastructures. For developers looking to build advanced communication features, integrating a
phone call api
or aVideo Calling API
can further enhance SIP-based solutions by enabling seamless voice and video experiences.Core SIP Network Elements:
- SIP Proxy Server: Forwards SIP requests and responses, enforces routing policies.
- SIP Registrar: Handles user registration and maintains location databases.
- SIP Redirect Server: Provides alternate routing information for SIP requests.
- Session Border Controller (SBC): Secures and regulates SIP traffic at network borders.
- Softswitch: Central call control for routing, billing, and policy enforcement.
- Media Gateway: Bridges SIP and legacy networks, handles media transcoding.
- Back-to-Back User Agent (B2BUA): Splits SIP dialogues for advanced control.
| Element | Primary Function | Typical Location | Security Role |
|---|---|---|---|
| SIP Proxy | Routing, signaling | Core network, edge | Limited |
| SIP Registrar | Registration, authentication | Core network | Moderate |
| Redirect Server | Call routing, load balancing | Core/edge | Low |
| SBC | Security, NAT, interoperability | Network edge | High |
| Softswitch | Call control, billing | Core network | Moderate |
| Media Gateway | Media bridging, transcoding | Edge (PSTN interconnect) | Moderate |
| B2BUA | Dialog control, mediation | Core/edge | High (in some cases) |
SIP Network Topology
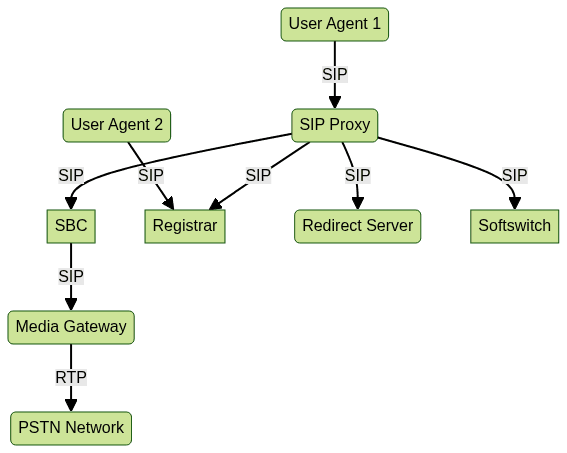
SIP Proxy Servers
SIP proxy servers are the workhorses of SIP signaling, tasked with forwarding SIP requests (like INVITE, BYE) and responses between endpoints. They enforce routing policies, support call forking, and may apply authentication and authorization. SIP proxies can be integrated with modern
Voice SDK
solutions to enable scalable, real-time audio communication in addition to traditional SIP signaling.- Stateless: Simply forward SIP messages without tracking session state; faster and more scalable.
- Stateful: Maintain session state for advanced routing, forking, and failover.
Proxies are deployed at both the core and edge of SIP networks, handling tasks from simple call routing to complex topology hiding in carrier-grade environments.
Sample SIP Proxy Configuration (OpenSIPS):
1# Route all incoming SIP calls to registrar or SBC
2route[default] {
3 if (is_method("REGISTER")) {
4 # Forward to SIP Registrar
5 forward("sip:registrar.internal.local");
6 exit;
7 }
8 if (is_method("INVITE")) {
9 # Apply routing logic, then forward to SBC
10 forward("sip:sbc.internal.local");
11 exit;
12 }
13}
14SIP Registrars and Redirect Servers
A SIP registrar authenticates and registers SIP endpoints (phones, softphones) by updating the location database with their current IP addresses. This enables dynamic user mobility and simplifies call routing by always knowing where a user is reachable. For those developing SIP clients on iOS, following a
callkit tutorial
can help you integrate native call handling and improve user experience.A SIP redirect server assists in efficient call routing and load balancing. It responds to SIP requests (like INVITE) with alternate destination information, allowing the originating proxy or endpoint to route the call elsewhere. This enables scalability and resilience in large deployments.
Deployment Tips:
- Integrate registrars with authentication backends (LDAP, RADIUS) for secure user management.
- Use redirect servers to offload routing complexity from proxies and enable geographic redundancy.
- Ensure tight integration between proxy, registrar, and redirect elements for seamless call setup.
Session Border Controllers (SBCs) in SIP Networks
Session Border Controllers (SBCs) are specialized devices or applications that sit at the network edge, protecting SIP infrastructures from external threats while solving interoperability issues. Their critical role includes supporting advanced features such as
embed video calling sdk
integration for rapid deployment of secure video and audio communication.Security Features
- Denial-of-Service (DoS) Protection: Detects and blocks malformed or excess SIP traffic.
- NAT Traversal: Facilitates SIP and RTP flow across NAT/firewall boundaries using techniques like STUN, TURN, and ICE.
- Encryption: Supports TLS (for SIP signaling) and SRTP (for media), ensuring privacy and integrity.
Interoperability and Protocol Normalization
SBCs normalize SIP messages between different vendor implementations, handle codec translation, and mediate between IPv4/IPv6 networks. This ensures seamless connectivity in heterogeneous environments.
Quality of Service (QoS) and Monitoring
SBCs can enforce QoS policies, prioritize voice traffic, and provide real-time call quality monitoring. Advanced SBCs offer analytics dashboards and alarms for proactive management.
SIP Call Flow with SBC
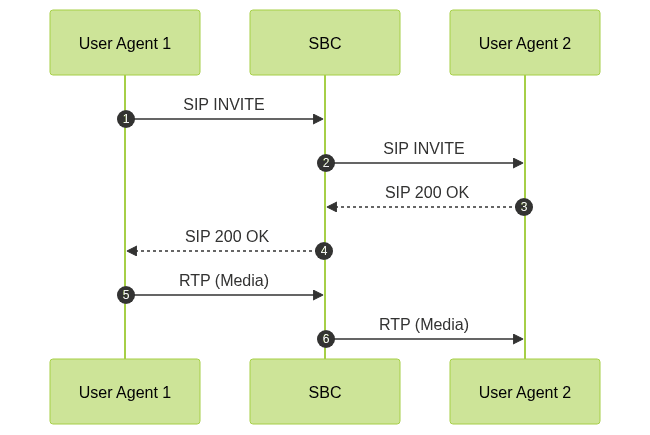
SBC Security Rule Example (Acme Packet)
1# Block SIP traffic from unauthorized IPs
2deny-from="0.0.0.0/0" except="203.0.113.10, 203.0.113.11"
3# Enable TLS for SIP signaling
4sip-tls-port=5061
5Softswitches and Media Gateways
Softswitches are central call control servers. They manage call setup, teardown, routing decisions, billing, and feature enforcement. They are used in both carrier and enterprise networks to orchestrate complex voice services. Developers building cross-platform SIP clients may benefit from exploring
flutter webrtc
to enable real-time audio and video communication in their applications.Media gateways bridge SIP/IP networks with legacy TDM (PSTN) systems, handling media stream translation, DTMF relay, and transcoding between codecs.
Carrier vs. Enterprise Deployments:
- Carriers use large-scale, redundant softswitches and gateways for high call volumes and SLA-driven services.
- Enterprises deploy smaller, integrated solutions for on-premises or hybrid VoIP.
Softswitch Routing Policy Example (Kamailio):
1# Example: Route calls based on destination prefix
2if ($rU=~"^1[0-9]{10}$") {
3 # US numbers, route to carrier A
4 forward("sip:carrier-a.sip.com");
5} else if ($rU=~"^44[0-9]{10}$") {
6 # UK numbers, route to carrier B
7 forward("sip:carrier-b.sip.com");
8}
9SIP Network Elements Security and Best Practices
Securing SIP network elements is crucial due to their exposure to public and partner networks. Common threats include:
- Toll Fraud: Unauthorized use of SIP trunks for expensive calls.
- DDoS Attacks: Flooding network elements to disrupt service.
- Eavesdropping: Intercepting SIP signaling or RTP streams.
For developers aiming to build secure and feature-rich SIP solutions, referencing a
phone call api
or following acallkit tutorial
can provide valuable insights into best practices and implementation strategies.SIP Security Hardening Checklist:
- Deploy SIP-aware firewalls and restrict access to trusted IPs.
- Enforce strong authentication (Digest, TLS).
- Regularly update SIP software and firmware.
- Enable logging and real-time monitoring for anomaly detection.
- Segment SIP network elements using VLANs or separate subnets.
- Employ SBCs at every network border.
- Use rate limiting and intrusion prevention where possible.
Monitoring platforms like Homer SIPCAPTURE or commercial SBC dashboards provide real-time analytics, helping detect and respond to threats promptly.
SIP Network Elements: Troubleshooting and Monitoring
Effective troubleshooting and monitoring are vital for maintaining high-availability SIP networks. Recommended tools and techniques:
- Packet Capture: Use Wireshark or tcpdump to inspect SIP and RTP traffic.
- Logs: Analyze proxy, SBC, and gateway logs for error patterns.
- Dashboards: Implement real-time monitoring (Homer, Grafana) for live status.
Common issues are one-way audio (often due to NAT or routing errors) and registration failures (authentication or network reachability problems). A systematic workflow involves isolating the element, analyzing logs/packets, and validating configuration or connectivity.
Implementation Example: Sample SIP Network Architecture
Let's walk through a practical SIP network setup integrating core elements:
- SIP Proxy handles initial signaling and policy-based routing.
- Registrar manages user registrations and location services.
- SBC secures the network edge, manages NAT, and ensures interoperability.
- Softswitch performs call control, billing, and advanced routing.
For organizations seeking to add video communication, integrating a
Video Calling API
can streamline the process and ensure compatibility with SIP elements.Configuration Highlights:
- Use DNS SRV for SIP element redundancy.
- Apply ACLs on all SIP elements.
- Enable logging and monitoring at each layer.
End-to-End SIP Network Architecture
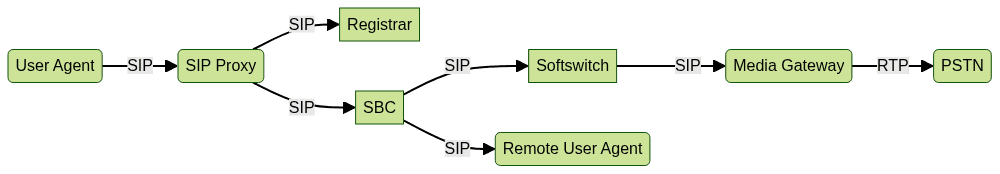
Conclusion and Next Steps
A well-designed SIP network leverages proxies, registrars, SBCs, softswitches, and gateways to deliver robust, secure, and scalable IP communications. Understanding each element's role, applying security best practices, and utilizing monitoring tools are key for success in 2025 and beyond. For further learning, explore open-source SIP platforms and vendor-specific documentation to deepen your implementation expertise. If you’re ready to build your own SIP-powered solution,
Try it for free
and start experimenting with modern communication APIs today.Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ