Introduction to SIP Networking
Session Initiation Protocol (SIP) networking is at the heart of today's real-time IP communications. As businesses and developers move away from traditional telephony, SIP networking has become foundational for Voice over IP (VoIP), video, instant messaging, and unified communications. The ability to establish, manage, and terminate multimedia sessions across the internet or private networks relies on SIP's robust signaling mechanisms. In this guide, we'll explore the architecture, protocol stack, session lifecycle, security, best practices, and troubleshooting for SIP networking in 2025.
What is SIP Networking?
Session Initiation Protocol (SIP) is an application-layer signaling protocol used to establish, modify, and terminate multimedia sessions such as voice, video, and messaging over IP networks. SIP networking orchestrates the setup and teardown of these sessions, handling user location, availability, and capabilities. Unlike circuit-switched traditional telephony, SIP networking leverages packet-switched networks, enabling flexibility, scalability, and integration with web and cloud technologies.
SIP networking's primary use cases include VoIP calling, video conferencing, presence information, instant messaging, and integration with unified communications (UC) platforms. SIP is often compared with protocols like H.323, but its simplicity, extensibility, and ease of integration have positioned it as the dominant protocol for real-time IP communications.
In a typical SIP networking scenario, endpoints (user agents) exchange SIP messages via intermediate servers (proxies, registrars, redirect servers) to negotiate session parameters and exchange media streams, usually transported over RTP (Real-time Transport Protocol). The protocol is transport-agnostic, supporting UDP, TCP, and TLS for secure signaling.
Key Components of SIP Networking
SIP Protocol Stack Overview
At its core, SIP operates at the application layer of the OSI model, relying on underlying transport and media protocols. Here's an overview of the SIP protocol stack:

- SIP Protocol: Handles session signaling.
- Transport Protocols: SIP can use UDP (default), TCP (for reliability), or TLS (for encryption).
- Media Transport: RTP or SRTP carries voice, video, or other media streams negotiated by SIP.
SIP Network Elements
SIP networking consists of several essential components:
- User Agents: SIP endpoints (softphones, IP phones, gateways) that initiate or receive sessions.
- SIP Proxies: Route SIP requests and enforce policies, enabling scalability and security.
- Registrars: Maintain a database of user locations (binding SIP addresses to IP addresses).
- Redirect Servers: Provide redirection to alternate SIP addresses or domains.
Basic SIP Message Example
A simple SIP INVITE message looks like this:
1INVITE sip:bob@example.com SIP/2.0
2Via: SIP/2.0/UDP pc33.example.com;branch=z9hG4bK776asdhds
3Max-Forwards: 70
4To: Bob <sip:bob@example.com>
5From: Alice <sip:alice@example.com>;tag=1928301774
6Call-ID: a84b4c76e66710
7CSeq: 314159 INVITE
8Contact: <sip:alice@pc33.example.com>
9Content-Type: application/sdp
10Content-Length: 142
11
12v=0
13o=alice 2890844526 2890844526 IN IP4 pc33.example.com
14s=-
15c=IN IP4 pc33.example.com
16t=0 0
17m=audio 49170 RTP/AVP 0
18SIP Session Lifecycle in Networking
Call Setup and Teardown
SIP networking sessions are initiated via a sequence of well-defined messages:
- INVITE: Starts a session.
- ACK: Confirms session establishment.
- BYE: Terminates the session.
These messages traverse SIP proxies and reach the destination user agent. Session teardown is as critical as setup, ensuring resources are freed and call state is consistent.
Media Negotiation and RTP
SIP negotiates session capabilities (codecs, transport) using Session Description Protocol (SDP) payloads within SIP messages. Once parameters are agreed, media streams (audio, video) are exchanged directly between endpoints using RTP. SIP handles signaling, while RTP carries the actual media.
Difference between Signaling and Media Paths
- Signaling Path: SIP messages between endpoints and proxies (may traverse multiple hops)
- Media Path: RTP streams flow directly between endpoints (where possible, unless relayed due to NAT/firewall)
SIP Call Flow Example
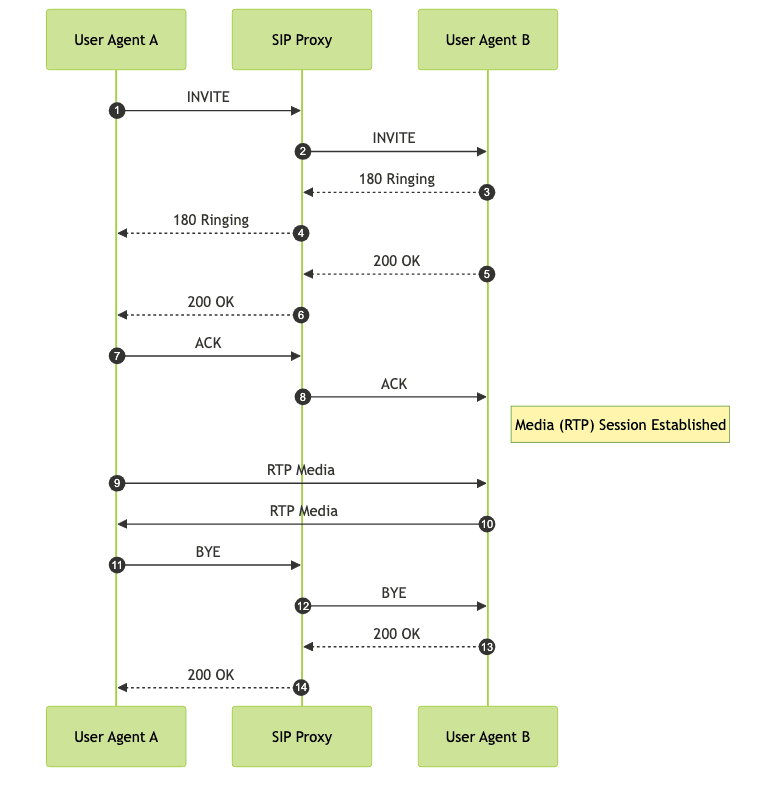
Implementing SIP Networking: Best Practices
Network Requirements and Configuration
Robust SIP networking requires careful network planning:
- Firewall/NAT Considerations: SIP and RTP often traverse firewalls and NAT devices. Solutions like STUN, TURN, and ICE help with NAT traversal. Ensure SIP-aware firewalls or Application Layer Gateways (ALGs) do not break signaling.
- QoS for VoIP and SIP: Prioritize SIP and RTP traffic using DSCP markings or VLANs to ensure low latency and high call quality. Monitor jitter, packet loss, and delay.
Security in SIP Networking
Securing SIP networking is critical for protecting sessions from eavesdropping, spoofing, and fraud.
- TLS Encryption for SIP: SIP over TLS encrypts signaling traffic to prevent interception and tampering.
- SRTP for RTP Media: Secure RTP (SRTP) encrypts media streams to protect voice and video content.
Example Config: Enabling TLS on a SIP Server (Asterisk)
1[general]
2enable_tls = yes
3tlsbindaddr = 0.0.0.0:5061
4tlsclientmethod = tlsv1_2
5
6[transport-tls]
7type = transport
8protocol = tls
9bind = 0.0.0.0:5061
10cert_file = /etc/asterisk/keys/asterisk.pem
11priv_key_file = /etc/asterisk/keys/asterisk.key
12method = TLSv1_2
13This configuration enables TLS on port 5061, using specified certificates for encrypted SIP networking.
Troubleshooting SIP Networking
SIP networking deployments can be complicated by NAT traversal, codec mismatches, or misconfigured firewalls. Common symptoms include call drops, one-way audio, or registration failures.
- NAT/Firewall Issues: Check SIP ALG settings, ensure proper port forwarding, or use ICE/STUN/TURN.
- Codec Mismatch: Verify supported codecs between endpoints.
- Diagnostic Tools: Use Wireshark to capture and analyze SIP and RTP traffic. SIP stack logs are invaluable for tracing signaling issues.
Code Snippet: Capturing SIP Traffic with Wireshark Filter
1sip || rtp || sdp
2Apply this display filter in Wireshark to isolate all SIP, RTP, and SDP packets, streamlining troubleshooting in sip networking environments.
SIP Networking in Enterprise and Cloud Environments
SIP networking forms the backbone of modern enterprise communications. SIP trunking enables organizations to connect their PBX systems to service providers over IP, reducing costs and increasing scalability. SIP integrates with unified communications (UC) platforms for voice, video, messaging, and collaboration.
Cloud-based SIP networking offers global reach, on-demand scaling, and integration with SaaS platforms. Enterprises leverage SIP for hybrid deployments, business continuity, and to enable remote workforces. Interoperability with legacy systems is achieved through SIP gateways and session border controllers (SBCs).
Conclusion: The Future of SIP Networking
The future of SIP networking is bright, driven by innovations in WebRTC, 5G, and IoT. As real-time communications expand across devices and platforms, SIP's adaptability ensures its continued relevance. Forward-thinking developers and architects will find SIP networking essential for powering the next generation of unified communications in 2025 and beyond.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ