Introduction to STUN and TURN Servers
In the ever-evolving landscape of real-time communications (RTC), enabling seamless peer-to-peer (P2P) connections is both a technical challenge and a necessity. Whether you’re building a video conferencing app, a VoIP solution, or a multiplayer game, connecting users directly—despite firewalls and network address translation (NAT)—is crucial for performance and user experience. STUN (Session Traversal Utilities for NAT) and TURN (Traversal Using Relays around NAT) servers are foundational technologies that make this possible in 2025, especially for protocols like WebRTC. This article explores what these servers are, how they work, and why they’re essential for modern networking.
What is NAT and Why is NAT Traversal Needed?
Network Address Translation (NAT) is a widely used networking technique where multiple devices on a local network share a single public IP address for accessing the internet. NAT conserves address space and adds a layer of security by masking internal IPs. However, this very mechanism introduces challenges for P2P communication, as external devices can’t directly reach hosts behind a NAT without special handling.
For example, in a home or office setup, your computer and phone might have private IP addresses like
192.168.1.10 and 192.168.1.11, but to the outside world, both appear as one public IP, managed by your router. This breaks direct inbound connections, which are vital for P2P applications.NAT traversal techniques—such as STUN, TURN, and ICE (Interactive Connectivity Establishment)—help overcome these challenges, enabling direct or relayed connections between endpoints, even in restrictive network environments. If you’re building cross-platform RTC apps, you might leverage solutions like
javascript video and audio calling sdk
to simplify integration and NAT traversal.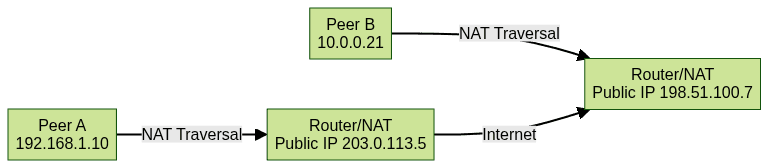
What is a STUN Server?
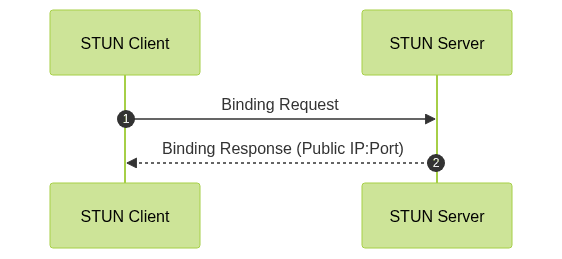
A STUN server (Session Traversal Utilities for NAT) is a lightweight network service that helps devices behind NAT discover their public-facing IP address and port. STUN is crucial for establishing direct peer-to-peer connections, particularly in scenarios where devices are behind different NATs and need to communicate over the internet.
The STUN protocol works by enabling a client to send a request to a STUN server located on the public internet. The server replies with the public IP and port it sees from the request, allowing the client to learn how it appears externally. This information is then shared (via a signaling server) with the peer, enabling both endpoints to attempt direct communication using techniques like UDP hole punching. For developers targeting mobile platforms, understanding how STUN works is essential, especially when implementing
webrtc android
solutions to enable real-time features on Android devices.STUN Protocol Basics and Message Flow
STUN operates over UDP and sometimes TCP, using simple request/response transactions. Here’s a typical message flow:
Example: STUN Request/Response in WebRTC (JavaScript)
1const pc = new RTCPeerConnection({
2 iceServers: [
3 { urls: ["stun:stun.l.google.com:19302"] }
4 ]
5});
6
7pc.onicecandidate = event => {
8 if (event.candidate) {
9 console.log("Found ICE candidate:", event.candidate);
10 }
11};
12Key Features and Use Cases of STUN Servers
- Enables direct P2P connections by revealing public IP and port
- Lightweight and low in resource consumption
- Widely used in VoIP,
video calling
apps, and online gaming for fast, low-latency communications - Developers working with cross-platform frameworks, such as
flutter webrtc
, also rely on STUN for seamless connectivity in their applications
Limitations of STUN Servers
- Cannot traverse symmetric NATs or very restrictive firewalls
- When direct connection fails, a TURN server is needed as a fallback
What is a TURN Server?
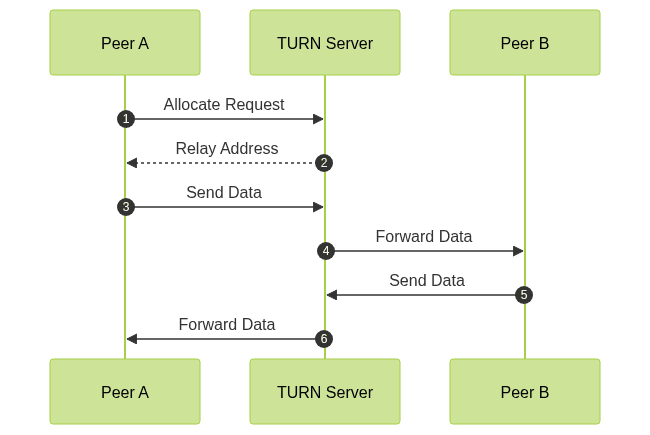
A TURN server (Traversal Using Relays around NAT) acts as an intermediary relay that forwards data between peers when direct communication is not possible—such as behind symmetric NATs or strict firewalls. Unlike STUN, which only assists in public IP discovery, TURN servers actually relay the entire media stream between clients.
TURN is essential for ensuring connectivity in the most challenging network environments. The protocol is an extension of STUN and provides additional methods for clients to allocate relay addresses and send/receive data through the TURN server. For those building mobile apps, using a
react native video and audio calling sdk
can help abstract away much of the TURN configuration, making it easier to ensure reliable connections.TURN Protocol Basics and Relay Communication
TURN operates over UDP, TCP, and even TLS, offering robust connectivity. Here’s a simplified view of TURN in action:
Example: TURN Configuration in WebRTC (JavaScript)
1const pc = new RTCPeerConnection({
2 iceServers: [
3 { urls: ["turn:turn.example.com:3478"], username: "user", credential: "pass" }
4 ]
5});
6Key Features and Use Cases of TURN Servers
- Provides reliable communication across highly restrictive NATs and firewalls
- Used as a fallback in the ICE process when STUN fails
- Essential in enterprise and corporate settings where security policies block P2P traffic
- TURN servers play a critical role in powering robust
Video Calling API
solutions, ensuring calls connect even in the most challenging network environments
Downsides and Considerations of TURN Servers
- Higher latency due to relayed traffic
- Increased bandwidth usage and operational costs (since all media is sent via the TURN server)
How STUN and TURN Work Together in ICE (Interactive Connectivity Establishment)
ICE (Interactive Connectivity Establishment) is a framework that coordinates the use of STUN and TURN to find the best path for data between peers. When two clients want to connect (e.g., in WebRTC), ICE gathers multiple connection options called "candidates":
- Host Candidates: Local IPs and ports
- STUN Candidates: Public-mapped addresses discovered via STUN
- TURN Candidates: Relay addresses allocated via TURN
ICE will first attempt direct connections using host and STUN candidates for low latency. If these fail (e.g., due to symmetric NAT or firewall), it will fallback to TURN candidates, ensuring connectivity even in the most difficult scenarios. For developers interested in integrating calling features into telephony apps, exploring a
phone call api
can provide additional insights into leveraging ICE for reliable audio connections.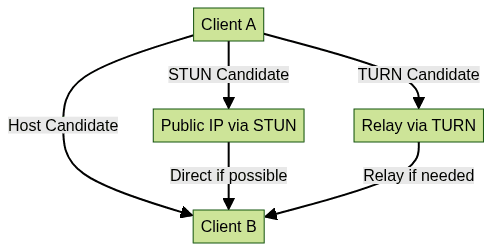
STUN vs TURN: Key Differences
| Feature | STUN Server | TURN Server |
|---|---|---|
| Main Purpose | Public IP discovery, NAT traversal | Data relay when direct fails |
| Data Path | Direct peer-to-peer | Relayed through TURN server |
| Resource Usage | Minimal | High (bandwidth, CPU, cost) |
| Use Cases | VoIP, video, gaming (open networks) | Enterprise, restrictive networks |
| Latency | Low | Higher (due to relaying) |
Implementing STUN and TURN Servers
When implementing STUN and TURN, you can choose between public/free servers (for testing or low-scale apps) and deploying your own (for reliability, security, and compliance). For those looking to quickly integrate RTC features, you can
embed video calling sdk
components into your application, which often handle much of the STUN/TURN configuration for you.Example: Using Public STUN/TURN Servers in WebRTC
1const pc = new RTCPeerConnection({
2 iceServers: [
3 { urls: ["stun:stun.l.google.com:19302"] },
4 { urls: ["turn:turn.example.com:3478"], username: "user", credential: "pass" }
5 ]
6});
7Basic Setup Steps
- Deploy the server (e.g.,
coturn
for TURN) - Configure network ports and TLS if needed
- Set strong authentication for TURN
- Regularly update and monitor for security
Security Best Practices
- Always require authentication for TURN
- Use TLS/DTLS to encrypt signaling and media traffic
- Restrict access to authorized apps and users
For developers building cross-platform RTC solutions, frameworks like
flutter webrtc
andreact video call
provide comprehensive guides and SDKs to streamline the implementation of STUN and TURN, making it easier to deliver high-quality real-time experiences.Conclusion
STUN and TURN servers are fundamental to enabling reliable, real-time peer-to-peer communication across the internet in 2025. By understanding their roles, strengths, and limitations, developers can choose the right combination for their applications—balancing performance, reliability, and cost. For most scenarios, combining both via ICE ensures robust connectivity regardless of network complexity.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ