Introduction to Sec-WebSocket-Key
The WebSocket protocol, standardized in RFC 6455, powers real-time, full-duplex communication over a single TCP connection. Unlike HTTP, which is request-response based, WebSockets enable persistent connections crucial for interactive web apps, gaming, financial platforms, and IoT. At the core of establishing a secure and compliant WebSocket connection lies the Sec-WebSocket-Key. This HTTP header is fundamental to the handshake process, ensuring protocol integrity and safeguarding against certain attack vectors.
In this comprehensive 2025 guide, we demystify the Sec-WebSocket-Key: what it is, how it works, its role in the protocol handshake, security implications, example implementations, common pitfalls, and how to troubleshoot related issues. Whether you’re building WebSocket servers or integrating client-side functionality, mastering Sec-WebSocket-Key is essential for robust, standards-compliant communication.
Understanding the WebSocket Handshake
The WebSocket handshake upgrades a standard HTTP connection into a persistent WebSocket connection. This process is governed by the WebSocket protocol (RFC 6455), which prescribes a specific HTTP-based handshake involving custom headers such as Sec-WebSocket-Key and Sec-WebSocket-Accept.
If you’re developing real-time communication features, you might also be interested in integrating a
Video Calling API
for seamless audio and video experiences within your applications.Handshake Process Overview
- Client Initiates Connection: The client sends an HTTP GET request with upgrade headers.
- Server Validates and Responds: The server checks headers, processes the Sec-WebSocket-Key, and replies with an HTTP 101 Switching Protocols response.
- Connection Established: Both parties switch to the WebSocket protocol for further communication.
Key headers involved include
Upgrade: websocket, Connection: Upgrade, Sec-WebSocket-Version, and most crucially, Sec-WebSocket-Key.WebSocket Handshake Flow
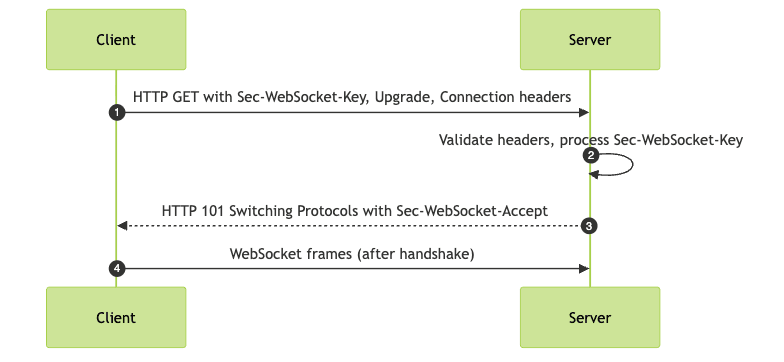
The handshake ensures both client and server agree to protocol semantics, using Sec-WebSocket-Key to verify compliance and prevent unauthorized upgrades.
What is Sec-WebSocket-Key?
Sec-WebSocket-Key is a critical HTTP header introduced in RFC 6455 as part of the WebSocket handshake. This header is a randomly generated, base64-encoded value sent from the client to the server in the initial handshake request. Its primary function is to ensure that only valid, protocol-compliant servers can successfully complete the handshake, thus preventing unauthorized or malicious protocol upgrades.
If you’re building real-time apps in Flutter, understanding
flutter webrtc
can help you leverage WebRTC for peer-to-peer communication, complementing your WebSocket-based architecture.Sec-WebSocket-Key appears in the client’s HTTP upgrade request. Here’s an example:
1GET /chat HTTP/1.1
2Host: server.example.com
3Upgrade: websocket
4Connection: Upgrade
5Sec-WebSocket-Key: dGhlIHNhbXBsZSBub25jZQ==
6Sec-WebSocket-Version: 13
7The value of Sec-WebSocket-Key is unique for each handshake, providing a mechanism for the server to prove compliance with the WebSocket protocol and protecting against certain classes of attacks. Without a properly formed Sec-WebSocket-Key, the server should reject the handshake to maintain protocol integrity.
How Sec-WebSocket-Key Works
The Sec-WebSocket-Key is generated by the client as a 16-byte random value, which is then base64-encoded. This ensures strong randomness and uniqueness for each WebSocket handshake. Here’s how the process unfolds:
- The client generates a random 16-byte value.
- This value is base64-encoded and set as the Sec-WebSocket-Key header.
- The server reads the key, processes it (see next section), and responds with a corresponding header.
For developers working with Android, exploring
webrtc android
can provide valuable insights into implementing real-time communication features that work seamlessly with WebSocket-based signaling.This mechanism improves protocol security by allowing the server to demonstrate knowledge of the key, making it harder for intermediaries or attackers to spoof or replay the handshake. While Sec-WebSocket-Key is not used for encryption, it is vital for handshake validation and protocol compliance.
The Relationship between Sec-WebSocket-Key and Sec-WebSocket-Accept
Upon receiving the Sec-WebSocket-Key, the server must generate a corresponding Sec-WebSocket-Accept header. This process involves critical steps that ensure the handshake’s authenticity and the server’s compliance with the protocol:
- Concatenation: The server appends the fixed GUID
258EAFA5-E914-47DA-95CA-C5AB0DC85B11to the received Sec-WebSocket-Key. - SHA-1 Hashing: The concatenated string is hashed using the SHA-1 algorithm.
- Base64 Encoding: The resulting hash is base64-encoded to produce the value of Sec-WebSocket-Accept.
This process guarantees that only servers aware of the protocol’s rules (and not generic HTTP servers or proxies) can correctly respond to the handshake.
If you’re interested in building interactive experiences beyond chat, consider integrating a
Live Streaming API SDK
to enable scalable, low-latency live video within your applications.Example: Generating Sec-WebSocket-Accept from Sec-WebSocket-Key
Here is a Node.js snippet demonstrating how a server computes Sec-WebSocket-Accept:
1const crypto = require('crypto');
2const secWebSocketKey = "dGhlIHNhbXBsZSBub25jZQ==";
3const GUID = "258EAFA5-E914-47DA-95CA-C5AB0DC85B11";
4const accept = crypto
5 .createHash('sha1')
6 .update(secWebSocketKey + GUID)
7 .digest('base64');
8console.log(accept); // Should output: s3pPLMBiTxaQ9kYGzzhZRbK+xOo=
9This value is sent back in the server’s handshake response:
1HTTP/1.1 101 Switching Protocols
2Upgrade: websocket
3Connection: Upgrade
4Sec-WebSocket-Accept: s3pPLMBiTxaQ9kYGzzhZRbK+xOo=
5Security Implications and Misconceptions
While the Sec-WebSocket-Key is vital for handshake validation, it is often misunderstood. It is not an authentication token, password, or encryption key. It does not provide confidentiality or user authentication. Instead, its primary role is to prevent replay attacks, protect against misbehaving intermediaries, and ensure the handshake comes from a compliant client and server.
If your use case involves integrating calling features, you might want to explore a
phone call api
to add voice call capabilities alongside your WebSocket-powered solutions.Sec-WebSocket-Key helps to:
- Prevent protocol downgrade and replay attacks by ensuring each handshake is unique.
- Distinguish WebSocket requests from generic HTTP requests, making it harder for proxies or attackers to spoof connections.
- Promote correct protocol implementation by requiring both parties to understand the handshake process.
However, for actual authentication or encryption, developers should implement higher-level security measures such as TLS (wss://) and token-based authentication.
Implementing WebSocket Handshake with Sec-WebSocket-Key
Let’s walk through implementing a WebSocket handshake, focusing on Sec-WebSocket-Key. Below are simplified server-side examples in Node.js and Python.
If you’re developing with React, you can enhance your real-time features by following this
react video call
guide, which demonstrates how to build scalable video calling solutions.Node.js Example
1const http = require('http');
2const crypto = require('crypto');
3
4const GUID = "258EAFA5-E914-47DA-95CA-C5AB0DC85B11";
5
6const server = http.createServer((req, res) => {
7 // Only handle WebSocket upgrade requests
8 if (req.headers['upgrade'] !== 'websocket') {
9 res.writeHead(400);
10 res.end('Not a WebSocket request');
11 return;
12 }
13 const key = req.headers['sec-websocket-key'];
14 const accept = crypto
15 .createHash('sha1')
16 .update(key + GUID)
17 .digest('base64');
18 res.writeHead(101, {
19 'Upgrade': 'websocket',
20 'Connection': 'Upgrade',
21 'Sec-WebSocket-Accept': accept
22 });
23 res.end();
24});
25
26server.listen(8080);
27If you’re looking for a robust, ready-to-use solution, check out the
javascript video and audio calling sdk
to quickly add real-time communication features to your web applications.Python Example (using standard libraries)
1import base64
2import hashlib
3from http.server import BaseHTTPRequestHandler, HTTPServer
4
5GUID = "258EAFA5-E914-47DA-95CA-C5AB0DC85B11"
6
7class WSHandler(BaseHTTPRequestHandler):
8 def do_GET(self):
9 if self.headers.get('Upgrade', '').lower() != 'websocket':
10 self.send_error(400, 'Not a WebSocket request')
11 return
12 key = self.headers['Sec-WebSocket-Key']
13 accept = base64.b64encode(
14 hashlib.sha1((key + GUID).encode('utf-8')).digest()
15 ).decode('utf-8')
16 self.send_response(101)
17 self.send_header('Upgrade', 'websocket')
18 self.send_header('Connection', 'Upgrade')
19 self.send_header('Sec-WebSocket-Accept', accept)
20 self.end_headers()
21
22httpd = HTTPServer(('localhost', 8080), WSHandler)
23httpd.serve_forever()
24For Python developers, the
python video and audio calling sdk
provides a comprehensive toolkit for integrating high-quality audio and video calls into your backend or cross-platform applications.Best Practices and Common Errors
- Always validate and sanitize incoming headers.
- Ensure the Sec-WebSocket-Key is exactly 16 bytes, base64-encoded.
- Respond only with HTTP 101 if all handshake headers are correct.
- Use existing WebSocket libraries in production for robust handling.
Common errors include missing or malformed keys, incorrect accept values, or failing to send proper upgrade headers. Debugging these often involves inspecting raw HTTP traffic or using protocol analyzers.
WebSocket Protocol Compliance and Browser Support
The WebSocket protocol, defined in RFC 6455, mandates the use of Sec-WebSocket-Key and Sec-WebSocket-Accept in the handshake. All major browsers—Chrome, Firefox, Edge, Safari, and Opera—fully support the protocol and enforce correct handshake semantics as of 2025.
If you’re building conferencing or collaboration tools, leveraging a
Video Calling API
can help you deliver reliable, high-quality video experiences across all supported browsers and devices.Major server frameworks (Node.js, Python, Java, Go, etc.) also support WebSockets and handle Sec-WebSocket-Key processing internally. When deploying, consider that reverse proxies (Nginx, HAProxy) must be configured to support WebSocket upgrades, relaying key handshake headers transparently.
Troubleshooting Sec-WebSocket-Key Issues
Developers often encounter handshake failures due to issues with the Sec-WebSocket-Key. Common problems include:
- Malformed or missing Sec-WebSocket-Key: Ensure the client sends a valid, base64-encoded 16-byte key.
- Incorrect Sec-WebSocket-Accept: Double-check your server’s hash and encoding logic.
- Proxy interference: Some intermediaries strip or modify headers; configure proxies for WebSocket compliance.
Debugging tips:
- Use tools like Wireshark or Chrome DevTools to inspect handshake requests/responses.
- Log raw headers for failed handshakes.
- Validate base64-encoded key length and format before processing.
If you want to experiment with these features in your own project,
Try it for free
and start building secure, real-time applications today.Conclusion: The Importance of Sec-WebSocket-Key in Secure WebSocket Connections
Sec-WebSocket-Key is indispensable for secure, standards-compliant WebSocket handshakes in 2025. While it doesn’t provide authentication or encryption, it validates protocol adherence, thwarts replay attacks, and ensures only legitimate parties establish WebSocket connections. Implement and troubleshoot it carefully for robust real-time applications.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ