Introduction to WebRTC IP Leaks
Web Real-Time Communication (WebRTC) is a powerful browser technology that enables real-time audio, video, and data communication between peers without the need for plugins. While it has revolutionized web-based communication, WebRTC introduces a significant privacy risk known as webrtc ip leaks. An IP leak occurs when your real IP address is exposed to external parties, even if you are using privacy tools like VPNs. For developers, engineers, and privacy-conscious users, understanding how webrtc ip leaks happen and how to mitigate them is critical in 2025's privacy landscape.
What is WebRTC?
WebRTC (Web Real-Time Communication) is an open-source project that provides browsers and mobile applications with simple APIs for real-time peer-to-peer communication. Unlike traditional communication methods that require external plugins or software, WebRTC is built directly into most modern browsers, enabling low-latency audio, video, and data sharing via JavaScript APIs. For developers building cross-platform solutions, technologies like
webrtc android
andflutter webrtc
offer robust options for integrating real-time communication into mobile apps.Common Use Cases
- Video and audio calls (e.g., Google Meet, Discord)
- Peer-to-peer (P2P) file sharing
- Live data sharing for collaborative apps and games
If you're looking to implement real-time communication in web applications, using a
javascript video and audio calling sdk
can streamline the process and ensure secure, high-quality connections.Underlying Protocols: STUN and TURN
WebRTC relies on several protocols to establish connections, especially across NATs (Network Address Translators) and firewalls:
- STUN (Session Traversal Utilities for NAT): Discovers your public-facing IP address and port.
- TURN (Traversal Using Relays around NAT): Relays data when direct P2P is not possible.
These protocols are essential for real-time communication but also play a key role in the privacy risk of webrtc ip leaks.
How WebRTC Causes IP Leaks
Browser Exposure of IP Addresses
Browsers use WebRTC to facilitate direct connections between peers. To do so, they enumerate and expose all available network interfaces, including:
- Public IP addresses (assigned by your ISP)
- Local IP addresses (e.g., 192.168.x.x or 10.x.x.x on your LAN)
This process can inadvertently reveal your actual public IP address, even when connected to a VPN, thus resulting in a webrtc ip leak. For those building cross-platform apps, leveraging a
react native video and audio calling sdk
can help maintain privacy and security across devices.Public vs Local IPs
- Public IP: The address visible to the wider internet, often masked by a VPN.
- Local IP: The internal address assigned by your router, typically not exposed online.
However, due to how WebRTC works, both can be leaked to websites via JavaScript using STUN requests.
STUN Requests and IP Exposure
When a browser initiates a WebRTC connection, it makes STUN requests to external servers to discover possible routes for direct P2P communication. The response from STUN servers includes your public and sometimes local IP addresses, which are then available to any web page running WebRTC JavaScript code.
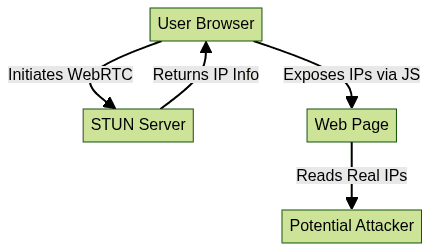
This diagram shows that by using the WebRTC API, a malicious website can read your real IP addresses—even if a VPN is active—leading to a webrtc ip leak.
Why WebRTC IP Leaks are a Privacy Risk
The exposure of your real IP address through webrtc ip leaks can have severe privacy implications:
- VPN Users: Many VPN users expect their real IPs to be hidden, but WebRTC can bypass this protection.
- Activists & Journalists: People working in sensitive environments can be exposed to tracking, surveillance, or censorship.
- General Users: Anyone concerned with online privacy can have their identity or location revealed through a subtle JavaScript API call.
For example, a user connected to a VPN may still have their real IP address leaked to a website through a WebRTC vulnerability, undermining the purpose of their VPN. Developers who want to add secure calling features to their apps can explore a
Video Calling API
to ensure privacy and minimize risks associated with IP leaks.Testing for WebRTC IP Leaks
How to Perform a WebRTC Leak Test
To determine if you are vulnerable to webrtc ip leaks, you can:
- Use online tools
- Run manual JavaScript code in your browser
If you are developing mobile or desktop applications, consider using
flutter webrtc
for secure and efficient real-time communication across platforms.Step-by-Step: Manual JavaScript WebRTC Leak Test
Open your browser console and run:
1// WebRTC IP Leak Test
2var pc = new RTCPeerConnection({iceServers:[]});
3pc.createDataChannel("");
4pc.createOffer().then(offer => pc.setLocalDescription(offer));
5pc.onicecandidate = function(event) {
6 if (event && event.candidate && event.candidate.candidate) {
7 console.log(event.candidate.candidate);
8 }
9};
10Look for lines containing
candidate with IP addresses. If you see your real public or local IP, your browser is susceptible to webrtc ip leaks.Recommended Online Tools
How to Prevent WebRTC IP Leaks
Disabling WebRTC in Different Browsers
Chrome
- Enter
chrome://flags/in the address bar - Search for "WebRTC"
- Set "WebRTC STUN origin header" to "Disabled"
- Alternatively, use the
WebRTC Network Limiter extension
Firefox
- Visit
about:config - Search for
media.peerconnection.enabled - Set it to
falseto disable WebRTC
Edge
- Enter
edge://flags/ - Search for "WebRTC"
- Disable related settings, or use extensions
Brave
- Go to
brave://settings/privacy - Toggle "WebRTC IP Handling Policy" to "Disable Non-Proxied UDP"
Opera
- Enter
opera://settings/ - Search for "WebRTC"
- Select "Disable non-proxied UDP"
For developers building Android apps,
webrtc android
provides guidance on implementing secure real-time communication while minimizing privacy risks.Using Browser Extensions
- uBlock Origin: Has advanced settings to block WebRTC
- WebRTC Network Limiter: Specifically limits WebRTC IP exposure in Chrome
- ScriptSafe, WebRTC Control: For additional privacy controls
If you need to add calling features to your app, exploring a
phone call api
can help you choose the best solution for secure and private audio communication.Pros and Cons
| Approach | Pros | Cons |
|---|---|---|
| Disabling WebRTC | Strong leak prevention, simple setting | Breaks real-time apps (calls, P2P) |
| Using Extensions | Flexible, easy to toggle, less intrusive | May miss some leaks, updates required |
| Custom Settings | Fine-grained control | Varies by browser, not always obvious |
Table: Browser Settings and Mitigation Options
| Browser | Native Setting | Extension Support | Can Fully Disable? |
|---|---|---|---|
| Chrome | No (flags/partial) | Yes (Network Limiter) | No |
| Firefox | Yes (about:config) | Yes (uBlock, etc.) | Yes |
| Edge | No (flags/partial) | Yes (some extensions) | No |
| Brave | Yes (settings) | Yes | Yes |
| Opera | Yes (settings) | Yes | Yes |
VPNs and WebRTC Leaks: What You Need to Know
Not all VPNs are created equal when it comes to webrtc ip leaks. Some VPNs route all traffic—including WebRTC traffic—through the encrypted tunnel, preventing leaks. Others only mask regular HTTP/S traffic, leaving WebRTC exposed.
If you’re building communication features for your app, integrating a
Video Calling API
can help you deliver secure, high-quality calls without exposing user IP addresses.What to Look for in a VPN
- Explicit protection against webrtc ip leaks (check provider documentation)
- Built-in firewall or IP leak protection
- Regular WebRTC leak testing in their apps
Why Not All VPNs Prevent Leaks
VPNs that do not block or reroute WebRTC STUN traffic can still leak your real IP. Always test your VPN for webrtc ip leaks after connecting.
Advanced Protection Tips
Using Firewall Rules
You can configure your OS or router firewall to block STUN/TURN server ports (generally UDP 3478, 5349), reducing the risk of webrtc ip leaks.
Blocking WebRTC at OS or Router Level
- Block UDP traffic on ports commonly used by WebRTC
- Use router-level firewall rules to prevent WebRTC traffic from leaving your network
For Developers: Restricting WebRTC in Web Apps
If you are developing a web application and want to minimize IP exposure:
1// Restrict WebRTC to relay (TURN) servers only
2const config = {
3 iceServers: [{
4 urls: ["turn:your.turn.server:3478"],
5 username: "user",
6 credential: "pass"
7 }],
8 iceTransportPolicy: "relay"
9};
10const pc = new RTCPeerConnection(config);
11Setting
iceTransportPolicy to relay ensures only TURN servers are used, preventing direct IP exposure. For a comprehensive approach to building secure video and audio features, consider using a javascript video and audio calling sdk
or areact native video and audio calling sdk
to leverage built-in privacy controls.Conclusion
WebRTC IP leaks remain a critical privacy risk in 2025. While WebRTC powers many innovative real-time applications, its design can inadvertently reveal your real IP address—even when using a VPN. By disabling WebRTC, using extensions, testing regularly, and configuring your browser and network, you can greatly reduce your exposure to webrtc ip leaks. Stay proactive and consistently monitor your privacy settings to ensure robust online protection.
If you’re ready to build secure, privacy-focused communication features,
Try it for free
and explore the latest solutions for video and audio calling APIs.Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ