VoIP Security & Encryption: The Complete Guide for 2025
Introduction to VoIP Security & Encryption
Voice over IP (VoIP) has revolutionized the way organizations and developers handle real-time communication. By transmitting voice and multimedia over IP networks, VoIP offers flexibility and cost savings, making it an integral part of modern IT infrastructure. However, this digital transformation comes with significant security and encryption challenges. As VoIP traffic traverses public and private networks, it is susceptible to interception, tampering, and a variety of cyber threats. Understanding VoIP security & encryption is essential to protect sensitive conversations, ensure privacy, and comply with industry regulations. This guide provides developers and IT professionals with actionable insights for implementing robust VoIP security in 2025.
Understanding VoIP Security Risks
Eavesdropping, Data Breaches, and Privacy Concerns
VoIP security & encryption are critical because voice packets are as valuable as data packets to attackers. Without encryption, VoIP calls can be intercepted, leading to unauthorized eavesdropping and potential data breaches. Privacy concerns escalate when confidential business negotiations, customer information, or sensitive personal data are at risk. Attackers can exploit unprotected VoIP channels, capturing audio streams and signaling data, resulting in reputational damage and regulatory penalties.
For developers building secure VoIP applications, leveraging a reliable
phone call api
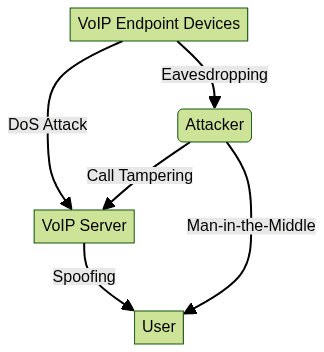
can help ensure robust security features are integrated from the start.Common Attack Types: DoS, Man-in-the-Middle, Call Tampering, Spoofing
VoIP systems face a spectrum of cyber threats:
- Denial of Service (DoS): Attackers flood VoIP servers, disrupting call services and causing outages.
- Man-in-the-Middle (MitM): Interceptors position themselves between endpoints to eavesdrop or alter call content.
- Call Tampering: Malicious actors inject noise, drop packets, or alter call parameters, degrading call quality.
- Spoofing: Attackers impersonate trusted users to gain unauthorized access or conduct fraud.
A lack of robust VoIP security & encryption measures can result in financial loss, compliance breaches, and loss of trust.
How VoIP Encryption Works
What is VoIP Encryption?
At its core, VoIP security & encryption involve converting voice and signaling data into encoded formats that can only be deciphered by authorized parties. Encryption ensures that even if traffic is intercepted, the information remains confidential and tamper-proof.
If you're developing cross-platform VoIP solutions, exploring technologies like
flutter webrtc
can help you implement secure, real-time communication features efficiently.Types of Encryption in VoIP: Signaling vs. Media
- Signaling Encryption: Protects call setup and teardown messages (such as SIP). Commonly uses TLS (Transport Layer Security).
- Media Encryption: Secures the audio/video stream itself, typically with SRTP (Secure Real-Time Transport Protocol).
- VPN Encryption: Encloses VoIP traffic within encrypted tunnels for added security across untrusted networks.
For Android developers, integrating
webrtc android
can provide a secure foundation for real-time voice and video communication.Encryption Algorithms & Protocols (SRTP, TLS, AES)
- SRTP: Encrypts and authenticates RTP streams, using algorithms like AES (Advanced Encryption Standard).
- TLS: Secures SIP signaling, preventing interception or manipulation during call negotiation.
- AES: A robust symmetric encryption algorithm, widely used in both SRTP and VPNs.
Example: SRTP Configuration in Asterisk
1[general]
2encryption=required
3srtpcapable=yes
4icesupport=yes
5media_encryption=sdes
6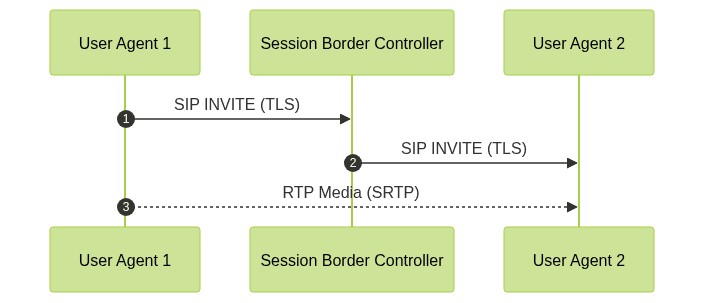
Essential VoIP Security & Encryption Best Practices
Choosing Secure VoIP Providers
When selecting a VoIP provider, prioritize those with comprehensive VoIP security & encryption measures. Look for:
- End-to-end SRTP and TLS support
- Transparent security policies and compliance certifications
- Regular security audits and incident response plans
If your application requires seamless integration of video communication, consider using a
Video Calling API
that offers built-in security and encryption features.Network Hardening: Firewalls, SBCs, VPNs
- Firewalls: Restrict and monitor VoIP traffic using strict rules to block unauthorized access.
- Session Border Controllers (SBCs): Provide deep packet inspection, protocol validation, and topology hiding to defend against attacks.
- VPNs: Securely tunnel VoIP traffic over untrusted networks, adding an extra encryption layer.
For developers targeting iOS, following a
callkit tutorial
can help you implement secure and native VoIP calling experiences on Apple devices.Strong Authentication & Access Control
Implement multi-factor authentication (MFA) for VoIP endpoints and administrative access. Enforce least-privilege principles and use strong, regularly rotated passwords or certificates.
To further enhance your application's audio capabilities, leveraging a
Voice SDK
can provide secure, scalable, and feature-rich voice communication.Regular Updates, Audits, and User Training
Maintain all VoIP software, firmware, and network devices with the latest security patches. Conduct periodic security audits to identify vulnerabilities. Educate users about phishing, social engineering, and safe communication practices to minimize human error risks.
If you want to quickly
embed video calling sdk
into your application, choose solutions that prioritize security and ease of integration.Implementation Guide: Securing Your VoIP System
Step-by-Step Checklist for VoIP Security & Encryption
- Network Segmentation: Isolate VoIP devices on dedicated VLANs to contain threats and reduce attack surfaces.
- Enable and Configure Encryption Protocols: Activate SRTP and TLS on all endpoints and servers. Verify end-to-end encryption is enforced.
- Deploy Firewalls and SBCs: Implement rules to allow only trusted VoIP traffic and block known attack vectors.
- Continuous Monitoring & Incident Response: Use SIEM tools to monitor call activity and detect anomalies. Establish rapid incident response procedures.
- Regulatory Compliance (HIPAA, GDPR): Ensure encryption and data protection measures meet regulatory requirements. Document policies and maintain audit trails.
For iOS developers, a comprehensive
callkit tutorial
can guide you through implementing secure VoIP call handling and system integration.Sample Firewall Rule for VoIP Traffic (iptables)
1# Allow SIP signaling (TLS encrypted)
2iptables -A INPUT -p tcp --dport 5061 -j ACCEPT
3
4# Allow SRTP media streams (RTP over UDP range)
5iptables -A INPUT -p udp --dport 10000:20000 -j ACCEPT
6
7# Block all other VoIP-related ports by default
8iptables -A INPUT -p udp --dport 5060 -j DROP
9Future Trends in VoIP Security & Encryption
AI, Machine Learning, and Zero Trust Models
In 2025, AI and machine learning are playing larger roles in identifying VoIP anomalies and adaptive threat detection. Zero Trust security models are being adopted, requiring continuous verification and minimizing implicit trust within VoIP networks.
Regulatory Landscape & Compliance Evolution
With growing privacy regulations like GDPR and HIPAA, compliance is evolving. VoIP providers and organizations must stay current with new data protection laws and regularly update security controls to maintain compliance.
Conclusion
VoIP security & encryption are vital for protecting modern communications from sophisticated threats. By understanding risks, implementing strong encryption protocols, and following best practices, developers and organizations can ensure their VoIP systems remain secure and compliant in 2025. Proactive adoption of these measures is crucial—start securing your VoIP environment today.
Try it for free
and experience secure, scalable VoIP solutions for your projects.Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ