Introduction to SIP TLS
Session Initiation Protocol (SIP) is the backbone of modern VoIP and unified communications systems, enabling voice, video, and messaging across IP networks. However, as SIP was initially designed for open networks, it is inherently vulnerable to threats like eavesdropping, spoofing, and tampering. This is where SIP TLS steps in. SIP TLS refers to running SIP signaling over Transport Layer Security (TLS), providing secure SIP signaling by encrypting SIP messages between endpoints and servers. Using SIP TLS is essential for maintaining privacy, integrity, and authenticity in SIP communications, ensuring that signaling data and credentials remain protected from attackers. In today's landscape, where secure SIP and SIP encryption are non-negotiable for compliance and business continuity, mastering SIP TLS is crucial for any IT or telecom professional.
Why Use SIP TLS?
Without SIP TLS, SIP signaling is transmitted in cleartext, exposing sensitive information like authentication credentials, phone numbers, and call details to anyone with network access. Attackers can exploit unencrypted SIP by intercepting, replaying, or manipulating signaling messages, leading to unauthorized calls, toll fraud, or even full compromise of VoIP systems. Implementing SIP TLS mitigates these vulnerabilities by encrypting SIP packets in transit, ensuring confidentiality and integrity. SIP TLS also provides endpoint authentication, preventing man-in-the-middle attacks. Compared to plain SIP over UDP or TCP, SIP TLS offers enhanced security, making it the de facto standard for secure SIP trunking and enterprise VoIP deployments in 2025. Organizations prioritizing secure SIP must implement SIP TLS to safeguard communications and meet regulatory requirements. For developers building secure VoIP solutions, leveraging a robust
phone call api
can further streamline integration and enhance call security.How SIP TLS Works
SIP TLS operates by encapsulating SIP protocol messages within a TLS session. Instead of using the default SIP port 5060, SIP TLS uses port 5061, signaling the use of encryption. SIP over TLS can be used in both client-server (endpoint-to-server) and server-server (proxy-to-proxy) scenarios. SIP URIs can explicitly indicate TLS usage via the
sips: scheme (e.g., sips:user@example.com), which mandates secure transport for the entire signaling path.The process starts with the TLS handshake, where both sides negotiate encryption parameters, exchange certificates, and establish a secure channel. Only after successful TLS negotiation does SIP signaling begin. This not only encrypts the signaling data but also authenticates the communicating parties based on their certificates. If you're developing SIP-enabled apps for mobile, exploring a
callkit tutorial
can help you integrate native call UI and enhance user experience on iOS devices.SIP TLS Handshake Example
1Client Server
2 | --- ClientHello --->
3 | <--- ServerHello ---
4 | <--- Certificate ---
5 | --- Certificate ---> (optional, for mutual auth)
6 | --- Key Exchange -->
7 | <--- Key Exchange --
8 | --- Finished ------>
9 | <--- Finished ------
10 | <--- SIP INVITE/SIP signaling over TLS --->
11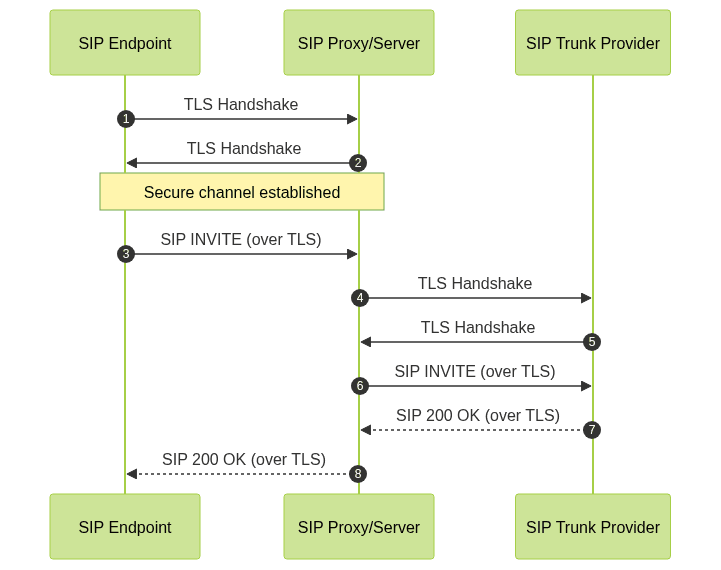
SIP TLS vs. SRTP: What's the Difference?
SIP TLS and Secure Real-time Transport Protocol (SRTP) address different parts of VoIP security. SIP TLS encrypts SIP signaling—the messages that set up, modify, and terminate calls—while SRTP encrypts the actual media streams (voice, video) during the call. Using SIP TLS alone only secures signaling, not the audio or video stream itself. For end-to-end VoIP security, both SIP TLS (for signaling) and SRTP (for media) should be used together. This dual approach protects against interception, replay, and spoofing of both call setup information and media content. If your application also requires secure video communication, consider integrating a
Video Calling API
to ensure encrypted media streams alongside SIP TLS.Step-by-Step SIP TLS Implementation
Prerequisites
To implement SIP TLS, you need a SIP platform that supports TLS transport—such as Asterisk, FreeSWITCH, 3CX, Cisco CUBE, or compatible IP phones and softphones. Proper certificate management is essential: use certificates signed by a trusted Certificate Authority (CA) or generate self-signed certificates for testing. The certificate's common name (CN) or subject alternative name (SAN) should match the Fully Qualified Domain Name (FQDN) of your SIP server. Ensure all devices and endpoints support SIP over TLS and have updated firmware. For those building custom voice solutions, leveraging a
Voice SDK
can simplify the process of adding secure, real-time audio features to your application.SIP TLS Setup: Asterisk
- Generate a Server Key and Certificate:
1openssl req -new -x509 -days 3650 \
2 -subj "/CN=sip.example.com" \
3 -nodes -out /etc/asterisk/keys/asterisk.pem \
4 -keyout /etc/asterisk/keys/asterisk.key
5- Configure
sip.conf:
1[general]
2tlsenable=yes
3tlsbindaddr=0.0.0.0:5061
4tlsclientmethod=tlsv1_2
5tlscertfile=/etc/asterisk/keys/asterisk.pem
6tlsprivatekey=/etc/asterisk/keys/asterisk.key
7tlscafile=/etc/asterisk/keys/ca.crt
8Restart Asterisk to apply changes. Ensure port 5061 is open and accessible.
SIP TLS Setup: FreeSWITCH
- Enable TLS Profile: Edit
sip_profiles/internal.xmlorsip_profiles/external.xml:
1<param name="tls" value="true"/>
2<param name="tls-sip-port" value="5061"/>
3<param name="tls-cert-dir" value="/etc/freeswitch/tls"/>
4- Place Certificates: Copy your server certificate and key into the directory specified above.
- Reload SIP Profiles:
1fs_cli -x "reloadxml"
2fs_cli -x "reload mod_sofia"
3SIP TLS Setup: 3CX
- Enable TLS in SIP Trunk Settings: In the 3CX Management Console, edit the trunk and select TLS as the transport type.
- Upload CA Certificate: Upload your CA root certificate to 3CX if required.
- Configure DNS/SRV Records: Make sure
_sips._tcpSRV records point to your 3CX FQDN for proper endpoint discovery.
SIP TLS Setup: Cisco
On Cisco CUBE or ISR routers, use the following commands:
1voice service voip
2 sip
3 transport tcp tls
4!
5crypto pki trustpoint SIP-CA
6 enrollment terminal
7 subject-name CN=sip.example.com
8!
9voice class tls-profile SIP-TLS
10 trustpoint SIP-CA
11!
12voice register pool 1
13 tls-profile SIP-TLS
14Ensure your router has the correct certificate chain installed and that the trustpoint is referenced in the TLS profile.
Configuring Endpoints
Most modern IP phones (Yealink, Polycom, Grandstream) and softphones (Zoiper, MicroSIP) support SIP TLS. In the phone's web UI or provisioning template, set:
- SIP transport: TLS
- SIP port: 5061
- Server FQDN: matches certificate CN/SAN
- CA certificate: uploaded if required
Example (Yealink provisioning):
1account.1.transport = 2 # 0=UDP, 1=TCP, 2=TLS
2account.1.sip_server.1.address = sip.example.com
3Restart the phone after saving changes. If you're working on Android applications, check out this
webrtc android
guide for implementing real-time communication features on mobile platforms.Certificate Management and Validation
Certificate management is critical to SIP TLS security. Always use certificates from a trusted CA in production; self-signed certificates are best for testing due to client trust issues. The certificate's common name or SAN must match the SIP FQDN to avoid validation errors. Maintain the complete certificate chain on your SIP server (server certificate + intermediate + root CA) so that endpoints can validate trust.
When a SIP endpoint connects, it validates the server certificate:
- Checks the validity period
- Verifies common name/SAN matches FQDN
- Confirms the chain up to a trusted CA
If validation fails, the client will reject the TLS connection.
Example: Certificate Validation Check (Linux)
1openssl s_client -connect sip.example.com:5061 -CAfile ca.crt -servername sip.example.com
2Look for
Verify return code: 0 (ok) in the output for successful validation. For those seeking alternatives to popular open-source conferencing solutions, exploring a jitsi alternative
can provide more flexibility and advanced features for secure communications.Common Challenges and Troubleshooting SIP TLS
SIP TLS deployments may face issues such as certificate errors (expired, mismatched CN), TLS handshake failures, or problems with DNS SRV records. Debugging these requires log analysis and network captures. Common problems include:
- Client trusts only specific CAs
- Incorrect FQDN in certificate
- Outdated TLS versions/ciphers
- NAT/SIP ALG interference
Troubleshooting Commands:
1# View Asterisk SIP TLS logs
2asterisk -rvvv
3sip set debug on
4
5# Test port and certificate with openssl
6openssl s_client -connect sip.example.com:5061
7
8# Capture SIP/TLS traffic
9sudo tcpdump -i eth0 port 5061 -n -vvv
10If you want to experiment with different SIP and VoIP APIs, you can
Try it for free
and evaluate which solution best fits your needs.Best Practices for SIP TLS Security
- Always use strong, modern TLS ciphers and protocols (e.g., TLS 1.2/1.3)
- Replace or renew certificates before expiration
- Regularly audit SIP TLS configurations and logs for anomalies
- Disable obsolete protocols (SSLv2, SSLv3, TLS 1.0)
- Ensure all endpoints and SIP proxies use trusted CA certificates
For developers building advanced calling features, reviewing a comprehensive
callkit tutorial
can help ensure seamless integration with native device capabilities. Additionally, selecting the rightphone call api
is essential for scalable and secure voice communications, and a reliableVideo Calling API
can further enhance your application's functionality.Conclusion
SIP TLS is the foundation of secure SIP signaling in 2025. By implementing robust SIP TLS configurations, managing certificates diligently, and following security best practices, you can ensure privacy and integrity for your VoIP communications.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ