SIP Protocol: The Ultimate Guide to Session Initiation Protocol for VoIP and Multimedia
Introduction to SIP Protocol
The SIP protocol—short for Session Initiation Protocol—underpins much of today's real-time communications across the internet. As the foundational signaling protocol for Voice over IP (VoIP) and multimedia sessions, SIP enables users to initiate, modify, and terminate voice and video calls, instant messaging, and other collaborative multimedia communication. Its flexibility and extensibility have made it the protocol of choice for service providers, enterprises, and developers seeking scalable, interoperable, and cost-effective solutions.
SIP is essential for connecting users, devices, and applications, playing a pivotal role in unified communications systems, IP-PBX deployments, and modern call centers. By separating signaling (SIP) from media transport (usually RTP), SIP ensures network independence and application-layer agility. As VoIP adoption accelerates in 2025, understanding how SIP protocol operates, its architecture, security aspects, and integration options is vital for IT professionals and software engineers building next-generation communication systems.
This guide delivers a comprehensive overview of SIP protocol, exploring its core concepts, message flow, security, practical implementation, and the future of SIP in a rapidly evolving digital landscape.
What is SIP Protocol?
The Session Initiation Protocol (SIP) is an open, standardized signaling protocol operating at the application layer of the OSI model. Its primary function is to establish, manage, and terminate communication sessions between endpoints—be they phones, computers, or software clients. SIP's versatility extends beyond voice calls, supporting video conferencing, presence information, instant messaging, and even online gaming sessions.
SIP utilizes a request-response model akin to HTTP, making it both human-readable and developer-friendly. Its role in session management includes negotiating capabilities, maintaining call states, and handling user registration. As a signaling protocol, SIP does not carry media streams; instead, it enables devices to discover one another and agree on session parameters before delegating media transport to protocols like RTP.
In essence, SIP protocol orchestrates the setup and teardown of real-time communication sessions, providing a robust framework for modern IP-based communications.
History and Evolution of SIP Protocol
The SIP protocol was first outlined in RFC 2543 (1999) and later standardized as RFC 3261 by the Internet Engineering Task Force (IETF). SIP emerged as a response to the limitations of legacy circuit-switched telephony, providing an IP-native alternative that leverages the flexibility and scalability of packet-switched networks.
Over time, SIP has evolved to address new requirements, including enhanced security, NAT traversal, and integration with other protocols like WebRTC. Its open, extensible nature has spurred widespread adoption for VoIP, video conferencing, and unified communications, shaping the direction of real-time communications on the internet.
SIP Protocol Architecture and Components
At the heart of the SIP protocol lies a modular architecture designed for interoperability and scalability. SIP defines several logical entities—each with a specific role in session management and signaling:
Key Components
- User Agent (UA): The endpoint device or application (e.g., softphone, VoIP desk phone) that initiates or receives SIP requests. It consists of two parts: User Agent Client (UAC) and User Agent Server (UAS).
- Proxy Server: An intermediary that routes SIP requests to the correct destination, enforcing policies and enabling load balancing.
- Registrar Server: Handles user registration, maintaining a location database mapping users to their current network addresses.
- Redirect Server: Directs SIP requests to the correct endpoint by providing client-side redirection.
- Location Server: Stores and retrieves user location information, often queried by proxy and registrar servers.
SIP Network Architecture Diagram
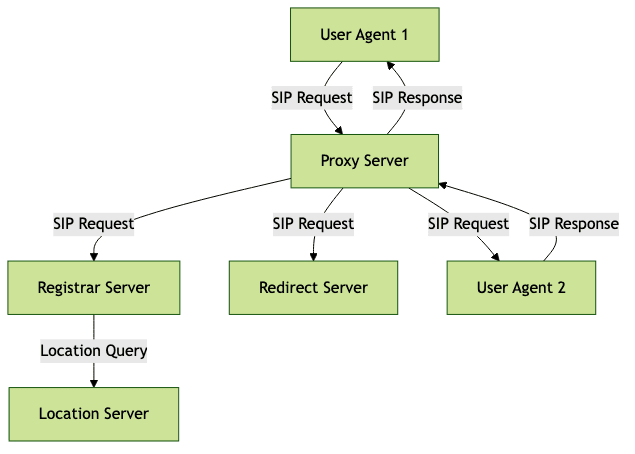
This architecture enables SIP to efficiently manage registrations, call routing, and session persistence, ensuring seamless communications across distributed networks.
How SIP Protocol Works: Message Flow and Methods
SIP protocol relies on a well-defined message format, using textual requests and responses exchanged between endpoints and servers. SIP messages fall into two categories: requests (from client to server) and responses (from server to client).
SIP Message Structure
A typical SIP message comprises:
- Start Line: Indicates request type (e.g., INVITE) or response code (e.g., 200 OK)
- Headers: Provide metadata (e.g., From, To, Call-ID, Contact)
- Body: Contains session description (often using SDP)
Common SIP Methods
- INVITE: Initiates a call/session
- ACK: Confirms session establishment
- BYE: Terminates a session
- REGISTER: Registers a user agent with a SIP registrar
- OPTIONS: Queries supported capabilities
SIP Headers and Message Format
Headers in SIP messages are critical for routing, authentication, and capability negotiation. Key headers include Via, From, To, Call-ID, CSeq, Contact, and Content-Type.
Example: SIP INVITE Message
1INVITE sip:alice@example.com SIP/2.0
2Via: SIP/2.0/UDP pc33.example.com;branch=z9hG4bK776asdhds
3Max-Forwards: 70
4To: Alice <sip:alice@example.com>
5From: Bob <sip:bob@example.org>;tag=1928301774
6Call-ID: a84b4c76e66710
7CSeq: 314159 INVITE
8Contact: <sip:bob@pc33.example.org>
9Content-Type: application/sdp
10Content-Length: 151
11
12v=0
13o=Bob 2890844526 2890844526 IN IP4 pc33.example.org
14s=-
15c=IN IP4 pc33.example.org
16t=0 0
17m=audio 49170 RTP/AVP 0
18SIP Call Flow: Step-by-Step
A typical SIP call flow involves:
- Registration: UA registers with the Registrar Server
- Call Setup: INVITE sent from Caller UA to Callee UA via Proxy
- Session Negotiation: 200 OK response, ACK confirmation
- Call Teardown: BYE request to end session
SIP Call Flow Sequence Diagram
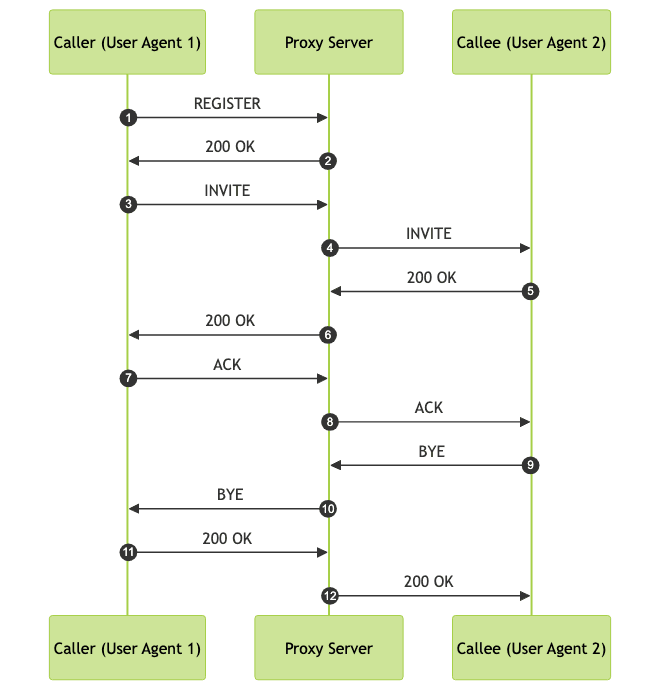
This sequence provides a clear view of SIP signaling from registration through call establishment and teardown.
SIP Protocol Transport: UDP, TCP, TLS
SIP protocol supports multiple transport protocols to suit different network requirements:
- UDP: Lightweight and fast; ideal for real-time voice but lacks congestion control and reliability.
- TCP: Reliable, connection-oriented; preferred for larger messages and environments with strict NAT/firewall policies.
- TLS: Encrypts SIP signaling over TCP, providing confidentiality and integrity for sensitive communications.
While UDP is common in VoIP, adopting SIP over TLS in 2025 is a best practice for securing signaling data, especially in enterprise and cloud environments.
SIP vs RTP: Signaling vs Media Transport
SIP protocol handles signaling—the setup, management, and termination of sessions—while RTP (Real-time Transport Protocol) carries the actual media streams (voice, video). SIP negotiates session parameters; RTP delivers the audio or video once the session is established.
In VoIP architectures, SIP and RTP work hand-in-hand: SIP sets up the call, and RTP streams the media, ensuring a seamless user experience across diverse networks and devices.
Key Features and Benefits of SIP Protocol
SIP protocol offers a range of advantages for VoIP and multimedia deployments:
- Cost Savings: Eliminates the need for dedicated telephony hardware and lines
- Scalability: Easily supports new users and endpoints
- Flexibility: Works across devices, networks, and geographies
- Interoperability: Open standard ensures compatibility between vendors
- Advanced Features: Conferencing, presence, instant messaging, and application integration
SIP's extensibility allows integration with web services, contact centers, and collaboration platforms, making it a cornerstone of unified communications in 2025.
SIP Protocol Security and NAT Traversal
Security is a central concern for SIP protocol deployments:
- SIP Security Threats: Eavesdropping, spoofing, and denial-of-service attacks
- Encryption: Use SIP over TLS to encrypt signaling, and SRTP (Secure RTP) for media streams
- NAT Traversal: SIP-aware firewalls and protocols like STUN, TURN, and ICE help maintain connectivity across NAT devices
Implementing strong authentication, regular patching, and secure transport is essential for defending against threats and ensuring reliable communications.
SIP Protocol Implementation: Practical Tips
Successful SIP protocol deployment requires careful planning:
- Choose Reliable Devices/Software: Select SIP-compliant phones, gateways, and servers from trusted vendors
- Configuration Best Practices: Use fully-qualified domain names, secure passwords, and limit open ports
- Troubleshooting: Monitor SIP logs for registration/authentication errors, validate network connectivity, and employ protocol analyzers like Wireshark for deep diagnostics
Proper SIP configuration and proactive monitoring help prevent common pitfalls and ensure seamless VoIP experiences.
Conclusion: The Future of SIP Protocol
In 2025 and beyond, SIP protocol remains at the heart of real-time communications—adapting to trends like cloud telephony, 5G integration, and AI-driven voice services. As a mature, extensible standard, SIP is well-positioned to power the next wave of unified communications and interactive media applications, ensuring its ongoing relevance in a connected world.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ