SIP Session: The Definitive Guide to Understanding SIP Sessions in VoIP and Multimedia (2025)
Introduction to SIP Sessions
The Session Initiation Protocol (SIP) has become the backbone of real-time communications, powering technologies such as Voice over IP (VoIP), video conferencing, and multimedia collaborations in 2025. As organizations seek scalable and interoperable solutions, SIP sessions serve as the fundamental building block for establishing, managing, and terminating multimedia interactions across diverse platforms. Whether you are a network engineer, VoIP developer, or IT architect, understanding SIP sessions is critical for designing robust communication systems. In this definitive guide, you will learn how SIP sessions work, explore their architecture, signaling flows, security considerations, and discover best practices for troubleshooting and real-world deployment.
What is a SIP Session?
A SIP session represents a logical connection established between two or more SIP endpoints (user agents) to exchange real-time multimedia content, such as voice, video, or messaging. It is created, managed, and terminated using a series of SIP messages that define parameters for the communication.
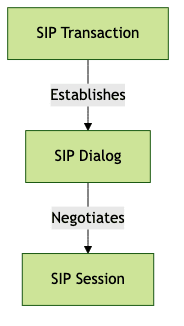
SIP Transaction vs. SIP Dialog vs. SIP Session
To clarify SIP terminology:
- SIP Transaction: A single request and all responses to that request (e.g., an INVITE and its responses).
- SIP Dialog: A peer-to-peer relationship between two user agents, established by specific SIP messages (INVITE, 200 OK, ACK). It tracks the state of the session.
- SIP Session: The actual exchange of media (voice, video, etc.) negotiated within a dialog.
Real-World Analogy
Think of a SIP session like a phone conversation: the process of dialing and connecting represents the dialog, the transaction is each exchange (like saying "hello" and getting a reply), and the session is the actual conversation—where information is shared.
SIP Session Architecture and Key Components
SIP User Agents and Servers
- User Agent Client (UAC): Initiates SIP requests.
- User Agent Server (UAS): Responds to SIP requests.
- SIP Proxy Server: Routes SIP messages between endpoints.
- Registrar Server: Handles user registrations.
- Location Server: Keeps track of endpoint locations.
SIP URI and Addressing
SIP uses SIP URIs (e.g.,
sip:alice@example.com) to identify users, much like email addresses. These are routed using DNS and SIP servers.SIP Session Signaling Flow
Session establishment begins with the INVITE message. Below is a basic SIP INVITE message:
1INVITE sip:bob@example.com SIP/2.0
2Via: SIP/2.0/UDP pc33.example.com;branch=z9hG4bK776asdhds
3Max-Forwards: 70
4To: Bob <sip:bob@example.com>
5From: Alice <sip:alice@example.com>;tag=1928301774
6Call-ID: a84b4c76e66710
7CSeq: 314159 INVITE
8Contact: <sip:alice@pc33.example.com>
9Content-Type: application/sdp
10Content-Length: 142
11
12v=0
13o=alice 2890844526 2890844526 IN IP4 pc33.example.com
14s=Session SDP
15c=IN IP4 pc33.example.com
16t=0 0
17m=audio 49170 RTP/AVP 0
18Where SDP and RTP Fit In
- SDP (Session Description Protocol): Negotiates media parameters (codecs, transport addresses) within SIP messages.
- RTP (Real-Time Transport Protocol): Transports media streams after the session is established.
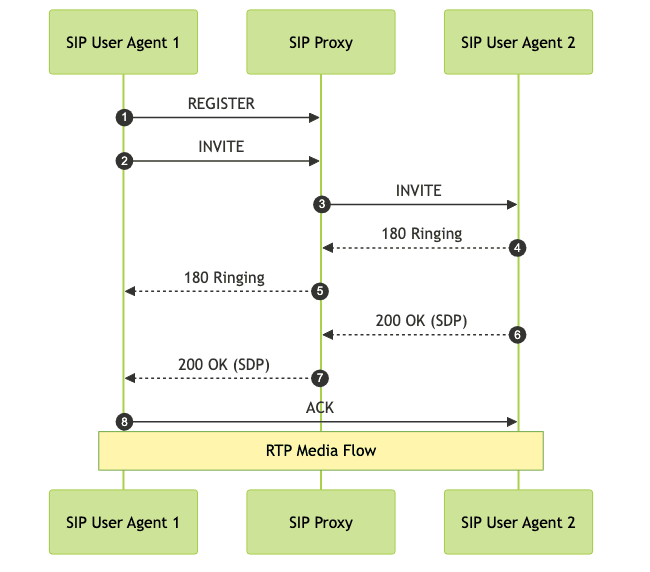
SIP Session Establishment: Step-by-Step
1. User Registration
Before establishing a SIP session, a user agent registers with a SIP registrar:
1REGISTER sip:example.com SIP/2.0
2Via: SIP/2.0/UDP pc33.example.com;branch=z9hG4bK776asdhds
3To: Alice <sip:alice@example.com>
4From: Alice <sip:alice@example.com>;tag=1928301774
5Call-ID: 1j9FpLxk3uxtm8tn@pc33.example.com
6CSeq: 1 REGISTER
7Contact: <sip:alice@pc33.example.com>
8Content-Length: 0
92. Call Setup (Session Initiation)
- INVITE: Initiates the session.
- 100 Trying: SIP server is processing the INVITE.
- 180 Ringing: Indicates the destination is being alerted.
- 200 OK: Accepts the session, includes SDP for media negotiation.
- ACK: Confirms the session establishment.
Message Flow Example
1INVITE sip:bob@example.com SIP/2.0
2...
3
4SIP/2.0 100 Trying
5...
6
7SIP/2.0 180 Ringing
8...
9
10SIP/2.0 200 OK
11Content-Type: application/sdp
12...
13
14ACK sip:bob@example.com SIP/2.0
15...
163. Media Negotiation with SDP
SDP is included in the INVITE/200 OK to agree on codecs and transport:
1v=0
2o=alice 2890844526 2890844526 IN IP4 pc33.example.com
3s=Session SDP
4c=IN IP4 pc33.example.com
5t=0 0
6m=audio 49170 RTP/AVP 0 8 97
74. Media Transport with RTP
Once the SIP session is established, RTP streams carry the actual audio/video between endpoints.
SIP Session Management and Termination
Modifying Sessions
- re-INVITE: Used to renegotiate media parameters during an active session (e.g., hold/resume).
- UPDATE: Can modify session parameters without changing media.
Ending Sessions with BYE
To terminate a SIP session, one party sends a BYE message:
1BYE sip:alice@pc33.example.com SIP/2.0
2Via: SIP/2.0/UDP pc36.example.com;branch=z9hG4bKnashds8
3From: Bob <sip:bob@example.com>;tag=456248
4To: Alice <sip:alice@example.com>;tag=1928301774
5Call-ID: a84b4c76e66710
6CSeq: 231 BYE
7Content-Length: 0
8Error Handling and Session Teardown
Common SIP error responses:
SIP/2.0 486 Busy HereSIP/2.0 404 Not FoundSIP/2.0 603 Decline
SIP Session Timers
Session timers (e.g., Session-Expires header) ensure sessions are alive and help clean up abandoned calls.
Troubleshooting Steps
- Analyze SIP call flow with tools like Wireshark
- Check registration and authentication
- Review SDP negotiation and codec compatibility
- Inspect NAT/firewall traversal issues
SIP Session Use Cases and Applications
VoIP Calls
SIP sessions are the foundation for VoIP telephony, enabling scalable and interoperable voice communication across the globe.
Video Conferencing
Modern video collaboration tools leverage SIP sessions for multi-party video, screen sharing, and interactive meetings.
Instant Messaging and Presence
SIP is used for text messaging, presence notification, and real-time chat in Unified Communications platforms.
IoT and Unified Communications
SIP sessions are increasingly used in IoT device communications and unified communications environments to link voice, video, and data workflows.
Security and Best Practices in SIP Sessions
Common SIP Session Vulnerabilities
- Eavesdropping on call content
- Registration hijacking and impersonation
- SIP message spoofing and DoS attacks
Security Mechanisms
- TLS (Transport Layer Security): Encrypts SIP signaling.
- SRTP (Secure Real-Time Transport Protocol): Secures RTP media streams.
- SIP Authentication: Uses Digest Authentication for verifying users.
Best Practices
- Enforce strong authentication and regular password changes
- Use TLS/SRTP end-to-end
- Limit SIP exposure with firewalls and SBCs (Session Border Controllers)
- Monitor and analyze SIP logs for anomalies
Conclusion
SIP sessions are the cornerstone of VoIP and multimedia communications in 2025, enabling flexible, scalable, and secure real-time interactions. By understanding SIP session architecture, signaling, management, and security considerations, engineers and developers can build reliable communication platforms. Continue learning through RFCs, SIP simulators, and open source tools to master SIP in your projects.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ