Introduction to VoIP Protocols
Voice over Internet Protocol (VoIP) has revolutionized modern communication by enabling voice, video, and messaging services to operate over IP networks rather than traditional telephony systems. At the heart of VoIP are specialized protocols—sets of rules and standards—that govern how voice packets are signaled, transmitted, and managed across networks. A VoIP protocol defines the method for signaling, session management, media transport, and device control, ensuring seamless real-time communication. As the demand for unified communications, IP telephony, and cloud-based collaboration grows in 2025, understanding VoIP protocols is essential for developers, network engineers, and IT professionals seeking robust, scalable, and secure communication solutions.
The VoIP Protocol Stack and Layered Model
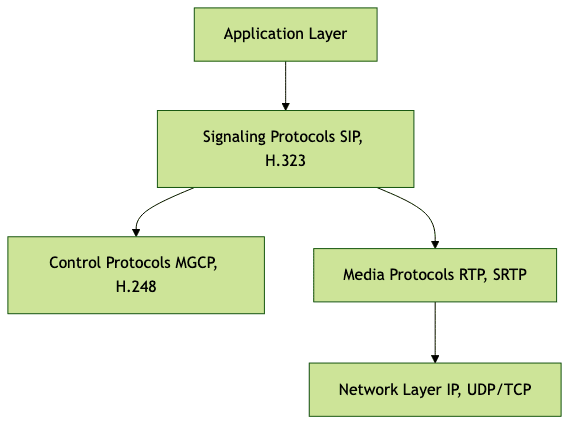
VoIP protocols are organized in a stack, similar in spirit to the OSI model, to separate signaling, media transport, and device control. This layered architecture ensures modularity, interoperability, and easier troubleshooting. In VoIP, each layer handles specific responsibilities, from initial call signaling and control, to actual media (voice/video) transmission, all the way to device management and integration with legacy PSTN systems.
While the OSI model has seven layers, the VoIP protocol stack typically focuses on:
- Signaling Layer: Handles call setup, teardown, and session management (e.g., SIP, H.323).
- Media Transport Layer: Transmits voice/video data in real time (e.g., RTP, SRTP).
- Control Layer: Manages media gateways and device control (e.g., MGCP, H.248).
- Application Layer: Encompasses codecs, application logic, and user interfaces.
This modular approach allows VoIP systems to mix and match protocols, optimizing for interoperability, quality of service (QoS), and security.
Core VoIP Protocols
Session Initiation Protocol (SIP)
SIP is the most widely adopted VoIP signaling protocol, responsible for establishing, modifying, and terminating multimedia sessions. SIP uses a text-based, HTTP-like request/response model, supporting both centralized and peer-to-peer architectures. It enables features such as call forwarding, conferencing, presence, and instant messaging.
SIP requests include INVITE (start session), ACK (confirm session), BYE (end session), and REGISTER (user location). Responses use status codes similar to HTTP.
1INVITE sip:bob@voip.example.com SIP/2.0
2Via: SIP/2.0/UDP pc33.example.com;branch=z9hG4bK776asdhds
3Max-Forwards: 70
4To: Bob <sip:bob@voip.example.com>
5From: Alice <sip:alice@voip.example.com>;tag=1928301774
6Call-ID: a84b4c76e66710@pc33.example.com
7CSeq: 314159 INVITE
8Contact: <sip:alice@pc33.example.com>
9Content-Type: application/sdp
10Content-Length: 142
11H.323 Protocol
H.323 is a comprehensive, ITU-T standardized protocol suite for voice, video, and data conferencing over packet-switched networks. It’s widely used in enterprise and carrier environments, especially for integrating with legacy systems. H.323 encompasses signaling, call control, RTP for media, and protocols for registration and directory services.
Real-Time Transport Protocol (RTP)
RTP is the core media transport protocol responsible for delivering audio and video streams over IP networks. It provides sequence numbering, timestamping, and payload identification to support real-time, jitter-free playback. RTP typically runs over UDP for low latency.
1|V|P|X|CC|M| PT| Sequence Number |
2| Timestamp |
3| SSRC identifier |
4| Contributing sources |
5RTP Control Protocol (RTCP) & Secure RTP (SRTP)
RTCP works alongside RTP to provide feedback on transmission quality, statistics, and participant information. SRTP extends RTP by adding encryption, message authentication, and integrity, ensuring secure media streams.
Supporting and Device Control Protocols
MGCP and H.248
MGCP (Media Gateway Control Protocol) and H.248/MEGACO are used to control media gateways bridging VoIP and legacy PSTN networks. They separate call control intelligence (handled by call agents or softswitches) from media conversion (handled by gateways), enabling scalable, centralized management. MGCP is deployed in carrier-grade VoIP, while H.248 supports more complex, scalable architectures such as IMS.
IAX/IAX2 and Proprietary Protocols
IAX/IAX2 (Inter-Asterisk eXchange) are optimized for trunking and NAT traversal in Asterisk-based PBX systems. Proprietary protocols like Cisco SCCP, Microsoft Lync, and Skype use custom signaling and media formats, often for enhanced features or closed ecosystems. While proprietary protocols can offer advanced capabilities, they may limit interoperability and scalability.
Session Description Protocol (SDP)
SDP is a companion protocol for negotiating media formats, codecs, and parameters within SIP or H.323 sessions. It describes session metadata such as codec types, RTP ports, and connection information.
Protocols in Practice: Establishing a VoIP Call
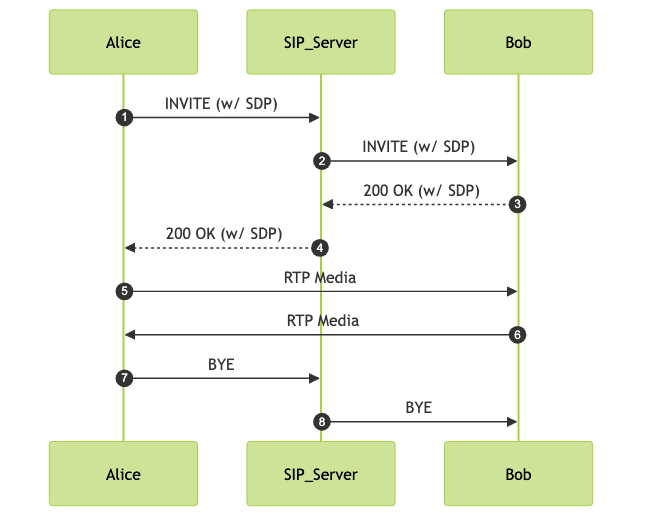
Establishing a VoIP call involves a sequenced interaction between endpoints and servers using multiple protocols. Here's a step-by-step overview:
- Signaling Initiation: Caller sends a SIP INVITE to the recipient's SIP server.
- Authentication & Routing: Server authenticates the caller and locates the callee.
- Session Negotiation: SIP exchanges include SDP payloads to negotiate codecs and media parameters.
- Call Setup: Recipient accepts the call, sending SIP 200 OK and SDP response.
- Media Channel Establishment: Both endpoints exchange RTP packets on agreed ports.
- Ongoing Monitoring: RTCP packets monitor quality; SRTP may secure the stream.
- Call Teardown: SIP BYE message terminates the session.
Security Considerations in VoIP Protocols
VoIP protocols must address a wide range of security threats, from eavesdropping and spoofing to denial-of-service attacks. Key mechanisms include:
- Encryption: SRTP secures media streams, while TLS encrypts SIP signaling.
- Authentication: SIP Digest Authentication and mutual TLS verify endpoints.
- NAT Traversal: Protocols like STUN, TURN, and ICE enable VoIP to function across firewalls and NAT devices.
- Vulnerabilities: Common risks include SIP flooding, RTP injection, and protocol fuzzing. Mitigation involves rigorous patch management, strong access controls, and network segmentation.
Securing VoIP is critical for privacy, regulatory compliance, and service reliability in 2025 and beyond.
VoIP Protocol Comparison and Selection Guide
When choosing a VoIP protocol, consider:
- SIP: Best for open, scalable, and interoperable deployments; widely supported by vendors and open source platforms.
- H.323: Ideal for legacy integrations and environments requiring robust, ITU-grade feature sets.
- MGCP/H.248: Suitable for centralized control of large-scale media gateways and PSTN bridging.
- Proprietary: Offers unique features but may lock you into a vendor ecosystem.
Evaluate based on scalability, interoperability, security, feature requirements, and long-term support for your use case.
Best Practices for Implementing VoIP Protocols
- Design networks with dedicated VLANs for VoIP traffic to reduce jitter and latency.
- Prioritize VoIP packets using QoS policies (DiffServ, VLAN tagging).
- Choose codecs that balance bandwidth and quality (e.g., Opus, G.722).
- Regularly update and secure protocol stacks; enable SRTP/TLS where possible.
- Monitor call quality (RTCP), packet loss, and network performance continually.
Conclusion
Mastering VoIP protocols is essential for building modern, secure, and scalable communication systems in 2025. The right protocol stack drives interoperability, QoS, and seamless user experiences.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ